This Project is build for Joyel and Joshua Master Applied Computer Science (MACS) students from Hochschule Schmalkalden - University of Applied Sciences Germany
Note
This project integrates the MITRE ATT&CK framework with advanced red team tactics to identify and exploit security vulnerabilities in Windows systems.
Tip
Use PowerShell scripts with advanced obfuscation techniques to create Fully Undetectable (FUD) payloads that can bypass Windows Defender.
Important
Regular updates to FUD payloads are necessary to keep up with the latest Windows security features and ensure continued effectiveness.
- Ubuntu Server Configuration for C2 and Mail Server
- Powershell Script to Payload.exe
- Python Script for Sending Mail with Payload.exe
- Metasploit Payload Generating
- Villain Payload
- Windows Defender Analysis Script
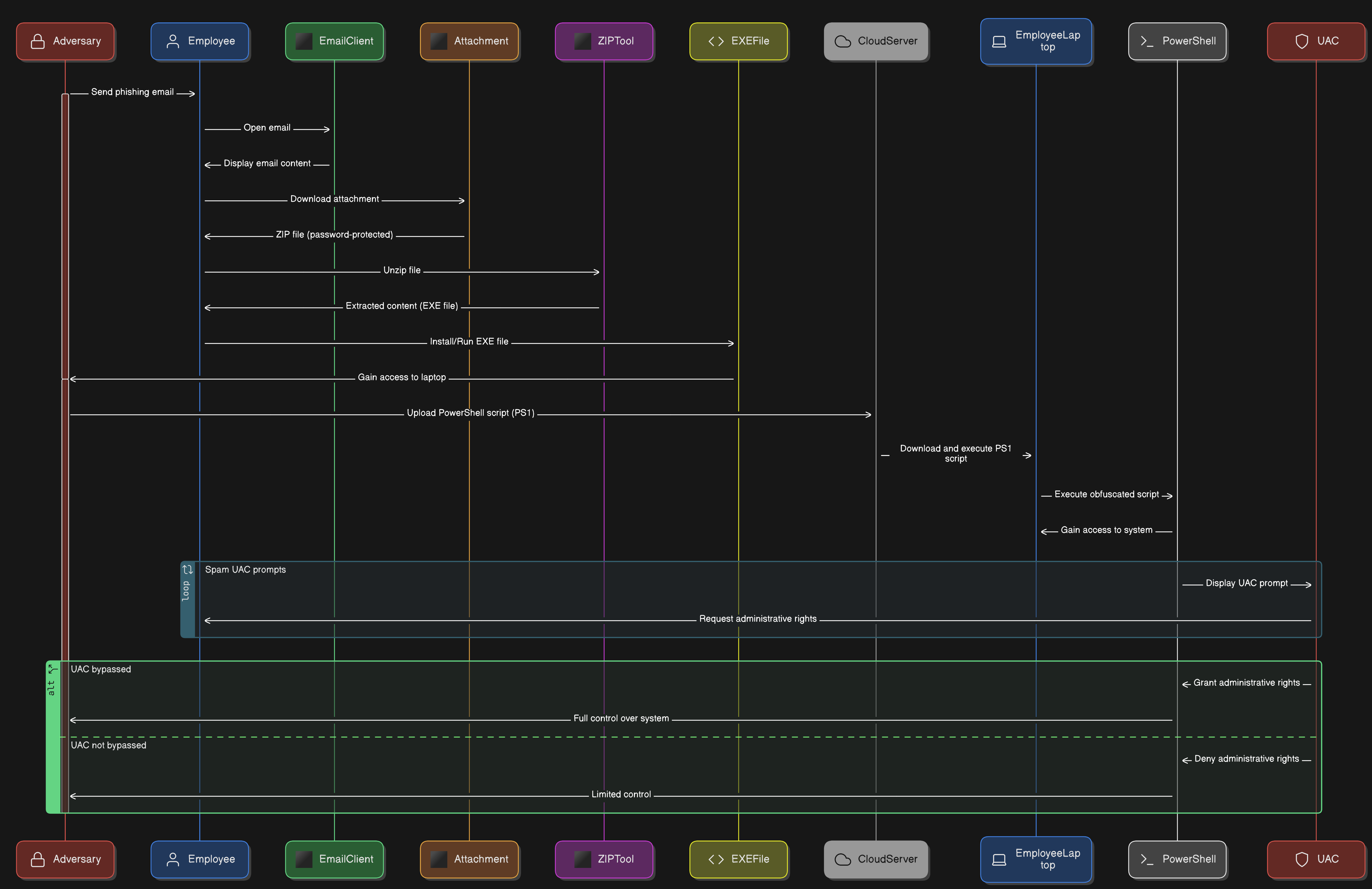
An adversary attempts to send a phishing email to technical support Employees of a XYZ company . One of the employees, who lacks cybersecurity knowledge, opens the email and downloads an attached file. The file is a password-protected ZIP archive. The employee manages to unzip the file and install or test the content within it. Meanwhile, the adversary gains access to the employee's company laptop. The adversary delivers a PowerShell script disguised as an executable (EXE) file. This script downloads a PowerShell script (PS1) from a cloud server into memory and executes it, bypassing detection by the employee and the default Windows security mechanisms. The PowerShell script is obfuscated to evade antivirus detection. Once the obfuscated script is running in memory, it gains access to the laptop and spams UAC (User Account Control) prompts to obtain administrative rights. After successfully bypassing UAC, the adversary gains full control over the system.
Important
Important
Important
ATT&CK Navigator File
Attack json file | download upload to ATT&CK Navigator for customization or for better view.
- The above attack can be improvised
- Effort calculated:- 100 hours 🕙 in 2.5 months 📆 [on-going porject]
Approximate value - Add delight to the experience when all tasks are completed
Warning
Simulated attacks in this project reveal potential vulnerabilities that adversaries might exploit, emphasizing the need for robust cybersecurity measures.
Caution
This project demonstrates sophisticated cyber-attacks, and its findings should be used responsibly to enhance defensive strategies and improve system security.
- scenario reference-01
- scenario reference-02
- MITRE ATT&CK®
- Attack-Naigator
- Windows 10/11 security update