Tornado Demo Vulnerable Application to test SQL injection vulnerability and patch it using RASP (Runtime Application Self-Protection)
Tornado Demo Vulnerable Application: Support Python 2.x & 3.x
RASP: Support Python 3.x only
How RASP works with the Demo Vuln App?
1.Hooking DbApi2 Call for execute() instruction.
2.Extract the Query from the execute (query)
For example
Query= SELECT * from users where userid=1
3.Lexical Analysis and token generation for the Query extracted from the execute() instruction
Using Lexer convert the query into token
Token = ['KEYWORD', 'WHITESPACE', 'OPERATOR', 'WHITESPACE', 'KEYWORD', 'WHITESPACE', 'STRING', 'WHITESPACE',
'KEYWORD', 'WHITESPACE', 'STRING', 'OPERATOR', 'NUMBER']
4.Run RASP in Learning mode to make it understand what is the Correct user input structure that need for application to work.
5.RASP will automatically insert the rules into separate database i.e rules.db while in Learning mode
6.Once application is reach the learning mode limitation i.e threshold limit, it will block no more rules to insert into
rules database while in leaning mode.
In my RASP Model, threshold limit for rules to insert into rules.db is 2 for demo purpose. so only two rules are allowed in rules database.
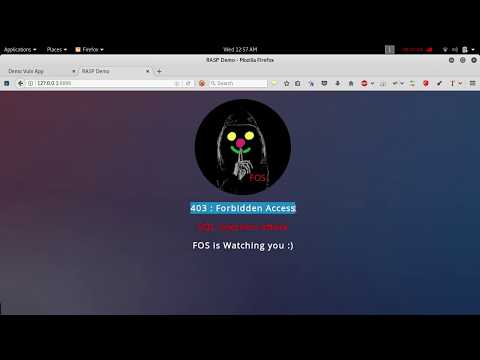
7.So now, we have have the rules ready to block SQL injection attack :)
8.Check the below video to see how it works... :)
- FOS Team : Fools of Security
Email address: umarfarookmech712@gmail.com | foolsofsecur1ty@gmail.com for more details.
Youtube: FOS
Blog: FOS