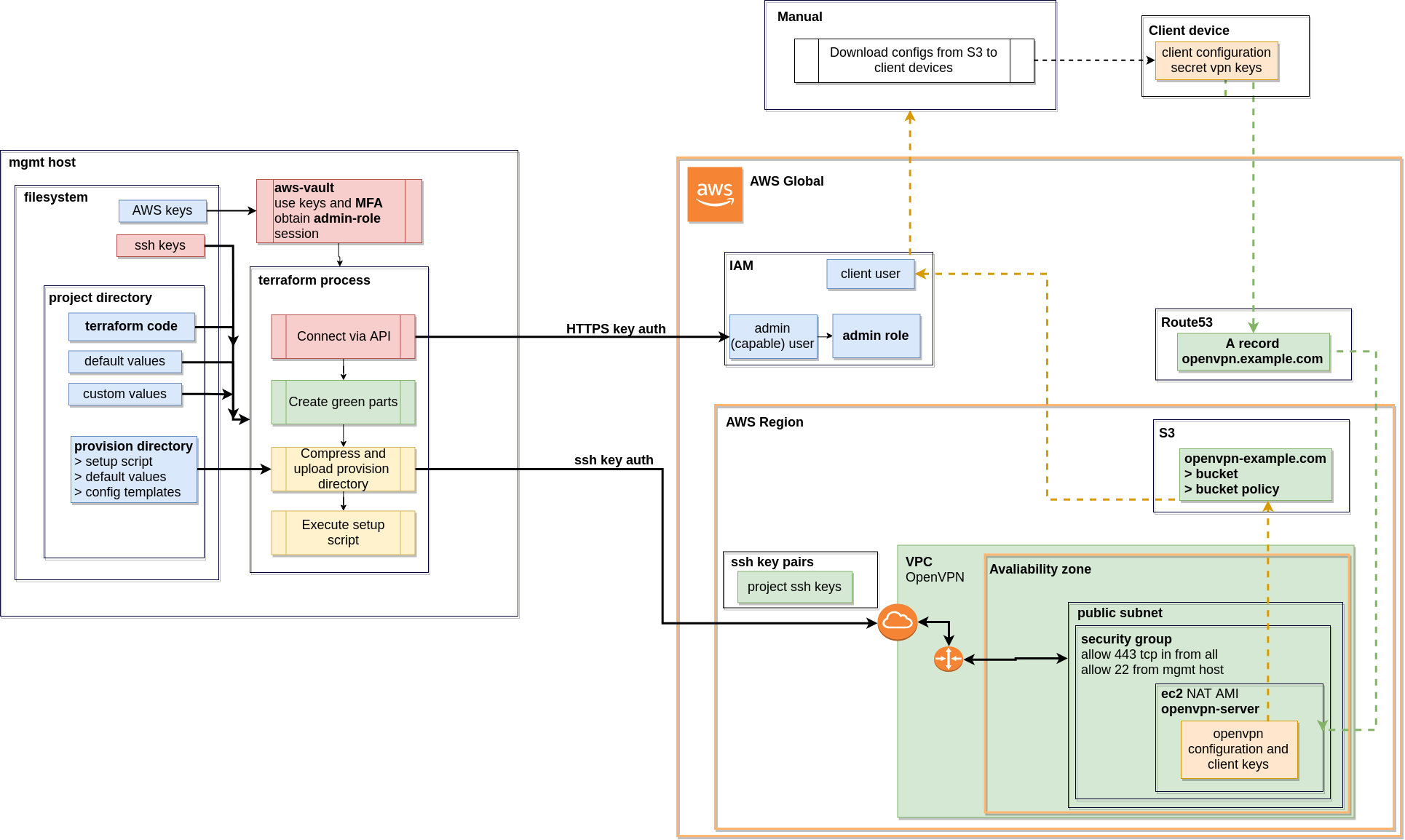
Automated creation of a simple OpenVPN infrastructure on AWS.
More secure Internet connections from diverse range of devices and access points.
- Set up a user with access keys (in my case auto_admin)
- Make sure the user can assume admin [role]
- Make sure the role requires MFA device, for example Google Authenticator
- You might find it useful to look at this Terraform Issue Comment
- Make sure the user can assume admin [role]
- Prepare a normal user, that will have access to generated OpenVPN configs
- User name should match value from iam_users variable set in terraform (below)
- User should have the following IAM policy attached
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:GetBucketLocation"
],
"Resource": [
"arn:aws:s3:::*"
]
}
]
}- Clone this repository
- Create a file with custom settings, for example example.auto.tfvars with values overriding defaults from variables.tf
# example.auto.tfvars
profile = "auto_admin"
aws_id = 210987654321
# ...- Finally execute
terraform init
aws-vault exec auto_admin -- terraform plan
aws-vault exec auto_admin -- terraform apply
- The code was created and tested on Linux Mint
- aws-vault v4.5.1
- Terraform v0.11.11
- The code assumes that it can access and use a preexisting domain configured in Route53
- Here is a diagram depicting the flow: