-
Notifications
You must be signed in to change notification settings - Fork 77
Secrets detection rules
The content on this page has moved: https://docs.sonarsource.com/sonarlint/visual-studio/using-sonarlint/rules/#secrets-detection
The SonarLint documentation has moved! Please visit https://docs.sonarsource.com/sonarlint/visual-studio/ to have a look at the new documentation website. We’ve improved the documentation as a whole, integrated the four SonarLint IDE extension docs together, and moved everything under the sonarsource.com domain to share a home with the SonarQube docs (SonarCloud to come in Q3 of 2023).
These GitHub wikis will no longer be updated after October 1st, 2023 but no worries, we’ll keep them around a while for those running previous versions of SonarLint for Visual Studio.
Starting with v6.4, SonarLint for Visual Studio will detect and report hard-coded cloud secrets as issues.
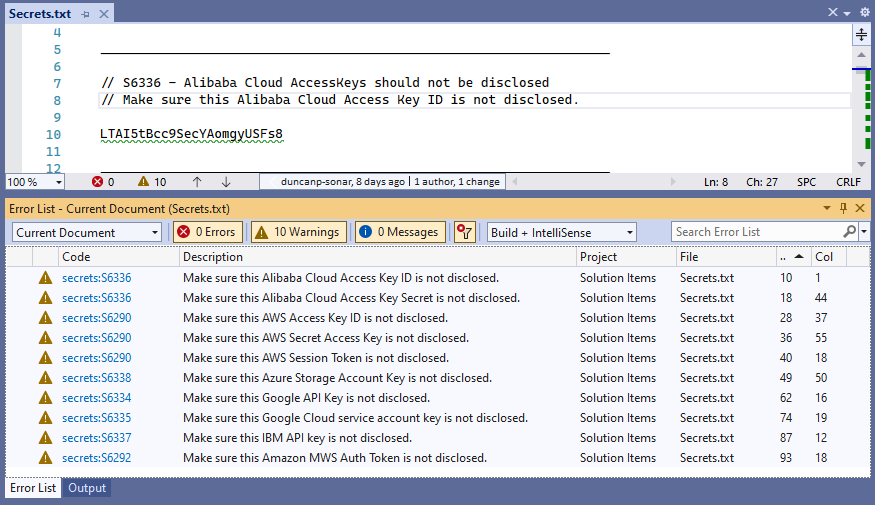
All types of text files are analysed, irrespective of the type of content (code, configuration, documentation etc). Analysis is triggered whenever a text file is opened or saved.
Documentation for individual rules can be found on the Rules website.
Secrets detection rules are only run in the IDE.
They do not appear in SonarQube/SonarCloud i.e. they can only be configured locally, and the secrets detection rules will not be run by the various Sonar scanners.
The rules can be enabled and disabled locally. It is not currently possible to suppress individual issues. See the rules configuration page for more information.