-
Notifications
You must be signed in to change notification settings - Fork 17
Deterministic key generation cscrypto
Generate a key pair or several using one of the seed (seed-phrase) from the dictionary bip39.
seed phrase:
- generation of random 256 bit data set
- 8-bit hash sum calculation
- concatenation of the resulting hash with seed (glue two lines), the so-called seed
further seed divided into 24 parts of 11 bits each
- each part is a binary representation of the number corresponding to the word from the https://github.com/bitcoin/bips/blob/master/bip-0039/english.txt dictionary (in the dictionary there are 2048 words = 2 ^ 11 so we split the seed into parts 11 bits)
- These words form a human-readable phrase (see example: chase motion picnic coffee violin cruise busy allow favorite rug sick hidden door heart elephant claw replace travel steel swallow energy dress orphan lesson); you can remember or write down this phrase.
key generation:
- In API_libsodium, a data set is transmitted (seed + id_wire). The use of such a seed representation makes it possible to create 2 ^ 64 keys for one seed of the phrase id_wallet - the wallet number for the seed.
Download gui cscrypto via the link https://github.com/CREDITSCOM/cscrypto/tree/master/qt/prebuilt
or gather together with the node
https://github.com/CREDITSCOM/node
you can find it in the / node / build / cscrypto / qt folder
Written in Qt. lin / win x64
- to generate new seed
- load seed from file
- all the keys on the keyboard
- generate public key from private
After entering the sid, it will be possible to generate keys according to the algorithm described above or replace the seed
- it is also possible to display the sid on the screen
- unload seed to file
- upload keys to a file readable by credits wallets

- generating the hash sums of any dataset
- message hashing
- file hashing
- HMAC is the authentication code (authentication) of messages using hash functions) password hashing. Verifying data by such a hash sum is possible only if a password is available.
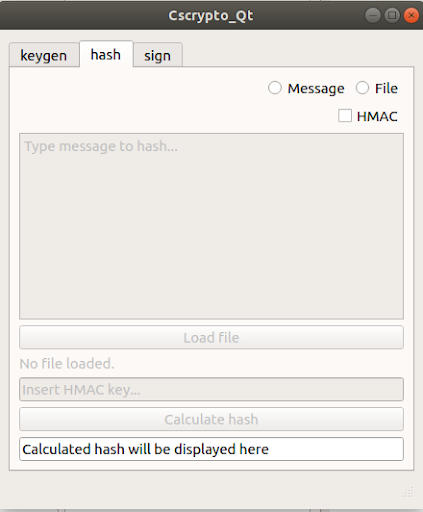
- sign the message or verify his signature
- sign / check file
- the ability to select the key of the generated using seed

comments
./client
No suitable keys were found. Type "g" to generate or "q" to quit.
Save this phrase to restore your keys in futute, and press any key to continue:
moral excuse chicken pitch quarter private arrange student expire exit talent power patient bean nasty logic melt february gadget employ shaft neck typical report - seed phrase on which you can later restore the keys through the utility cscrypto.
then the program will offer to encrypt the keys (it is very important to perform encryption, the node needs the keys in the file to work in the system, it is strongly not recommended to keep the keys in the unencrypted form)
Choose your private key file encryption type (enter number):
[1] Encrypt with password (recommended)
[2] No encryption
[q] Quit
Enter choice: 1
You can encrypt keys with a password or a file (any file).
To use password for encrytion/decryption press "p", to use file press "f": p
Enter password: ***
Confirm password: ***
Or using a file
To use password for encrytion/decryption press "p", to use file press "f": f
Enter path to file (will be used as cipher key):home/user/test.***
During encryption, you can also display the keys on the screen unencrypted.
Keys generated
To show your keys not encrypted press "s".
Seconds left:
1.74425s
Press any key to continue...
PublicKey: ваш кллюч PrivateKey: ваш кллюч
run the program
Restart client
./client
The key file seems to be encrypted
To use password for encrytion/decryption press "p", to use file press "f": p
Enter password: ***
Trying to open file…
As soon as decryption begins, you will be prompted to press p to change:
To change password press "p".
Seconds left:
Encrypting the private key file with new password…
You can encrypt keys with a password or a file (any file).
To use password for encrytion/decryption press "p", to use file press "f": p
Enter password: ***
Confirm password: ***
Or using a file
To use password for encrytion/decryption press "p", to use file press "f": f
Enter path to file (will be used as cipher key):home/user/test.***
During encryption, you can also display the keys on the screen unencrypted.
Keys generated
To show your keys not encrypted press "s".
Seconds left:
1.74425s
Press any key to continue...
PublicKey: ваш кллюч PrivateKey: ваш кллюч
run the program
To restore, use the cscrypto utility.
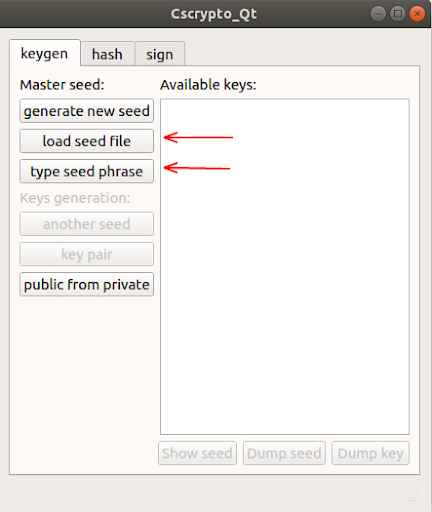
enter the seed phrase manually

or download a text file with seed phrase
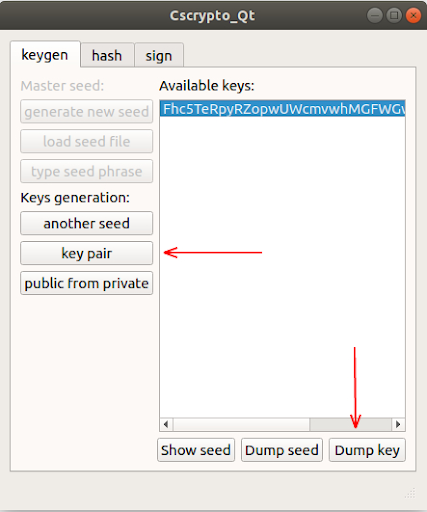
generate the key pair key and upload it to the key.json file
- key - the name of your key
the first key will be your key node
This is the Argon2 algorithm. It is used to get an encryption key from a file or password. Roughly speaking, we consider the file hash or password hash in a special way. On a 2.8 Ghz Core i7 CPU, it takes approximately 3.5 seconds to generate the necessary key and 1 GB of RAM is used. Then we use this generated key together with a random salt for a symmetric authentic stream encryption. Encryption algorithm chacha20, authentication algorithm poly1305.
https://tools.ietf.org/html/draft-agl-tls-chacha20poly1305-04
You can use a file up to 4 GB!!!