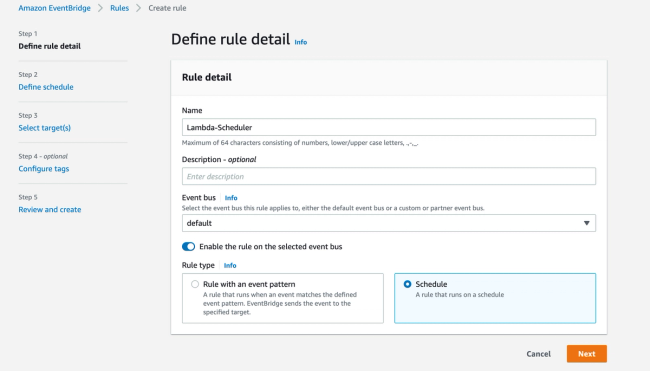
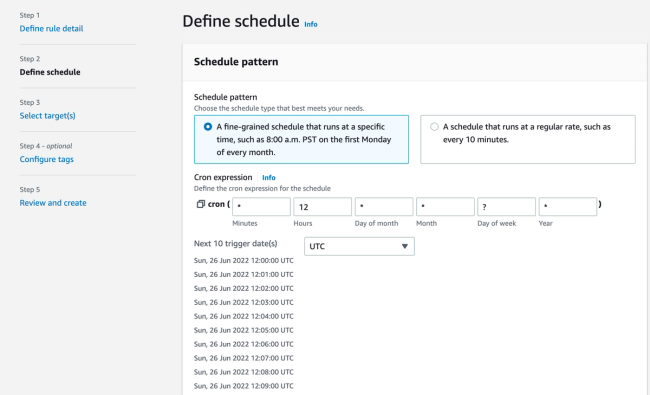
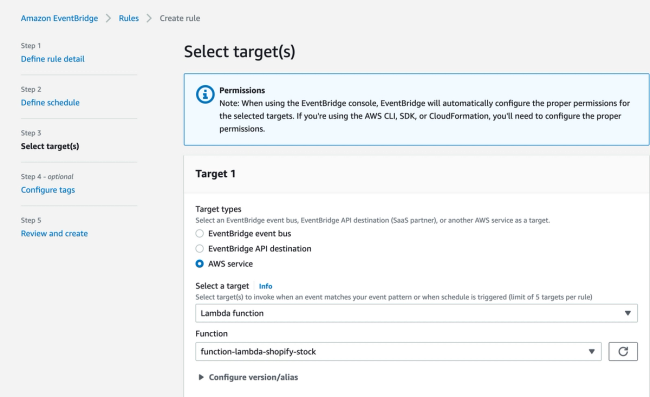
AWS Command Line Interface(CLI) is used in this post to deploy the Lambda function. CLI needs to be installed and configured locally in order to use it.
AWS Shell helps with auto-completion, fuzzy searching, and more.
We're uploading the Go binary file into AWS Lambda as a .zip file. In order to build for Linux, we're using the following command.
GOOS=linux GOARCH=amd64 go build -o main main.go
zip main.zip mainCreate the assume-role-policy.json file:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}Create an IAM role
iam create-role --role-name role-lambda-shopify --assume-role-policy-document file://assume-role-policy.json
{
"Role": {
"Path": "/",
"RoleName": "role-lambda-shopify",
"RoleId": "AROARKDOZJ3E6FZQIORPR",
"Arn": "arn:aws:iam::090426658505:role/role-lambda-shopify",
"CreateDate": "2022-06-25T21:30:57Z",
"AssumeRolePolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "lambda.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
}
}
Let's attach permission to this role. AWSLambdaBasicExecutionRole gives permission to write logs to cloudWatch.
iam attach-role-policy --role-name role-lambda-shopify --policy-arn arn:aws:iam::aws:policy/service-role/AWSLambdaBasicExecutionRoleCreate an SNS topic
sns create-topic --name shopify-stock-notification
```json:response
{
"TopicArn": "arn:aws:sns:ap-southeast-2:090426658505:shopify-stock-notification"
}To subscribe to the SNS topic:
sns subscribe --topic-arn arn:aws:sns:ap-southeast-2:090426658505:shopify-stock-notification --protocol email --notification-endpoint test@hotmail.comwe're going to attach an inline policy that grants access to the Lambda function to trigger SNS notification.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "sns:Publish",
"Resource": "arn:aws:sns:ap-southeast-2:090426658505:shopify-stock-notification"
}
]
}
iam put-role-policy --role-name role-lambda-shopify --policy-name publish-to-sns --policy-document file://sns-policy-for-lambda.jsonCreate/Update Lambda function
lambda create-function --function-name function-lambda-shopify-stock --zip-file fileb://main.zip --handler main --runtime go1.x --role arn:aws:iam::090426658505:role/role-lambda-shopify{
"FunctionName": "function-lambda-shopify-stock",
"FunctionArn": "arn:aws:lambda:ap-southeast-2:090426658505:function:function-lambda-shopify-stock",
"Runtime": "go1.x",
"Role": "arn:aws:iam::090426658505:role/role-lambda-shopify",
"Handler": "main",
"CodeSize": 6662556,
"Description": "",
"Timeout": 3,
"MemorySize": 128,
"LastModified": "2022-06-25T22:04:02.491+0000",
"CodeSha256": "uLsOQEp4VCFi294HpbKyl1i60uLGUIBwmpI2cg0wdeU=",
"Version": "$LATEST",
"TracingConfig": {
"Mode": "PassThrough"
},
"RevisionId": "1ff52d69-6429-49d8-ba7f-492886e9aee3",
"State": "Pending",
"StateReason": "The function is being created.",
"StateReasonCode": "Creating",
"PackageType": "Zip",
"Architectures": [
"x86_64"
],
"EphemeralStorage": {
"Size": 512
}
}
To add environmental variable to Lambda function:
lambda update-function-configuration --function-name function-lambda-shopify-stock --environment "Variables={SHOPIFY_API_KEY=<your-shopify-key>, SHOPIPY_API_PASSWORD=<your-shopify-password>, SHOPIFY_SHOPIFY_DOMAIN=c<your-shopify-domain>}”To update the Lambda function:
lambda update-function-code --function-name function-lambda-shopify-stock --zip-file fileb://main.zipTo invoke the Lambda function and store the output to a text file:
lambda invoke --function-name function-lambda-shopify-stock output.txtEventBridge rule let you create a cron that triggers the Lambda function.