-
Notifications
You must be signed in to change notification settings - Fork 214
Infrastructure Dashboard Reports
-
Azure Infrastructure Dashboard - Report Pages
- CCO Azure Infrastructure Dashboard overview page
- Azure Advisor Recommendations page
- Azure Defender Alerts page
- Azure Compute Overview page
- Azure VNETs and Subnets Recommendations page
- Azure Network Security Groups page
- Azure App Services page
- Role Based Access Control page
- Service Principal Role Based Access Control page
- IaaS Usage and Limits page
- IaaS Idle Resources Dashboard page
- Azure Kubernetes Service Dashboard Overview page
- Azure Kubernetes Service page
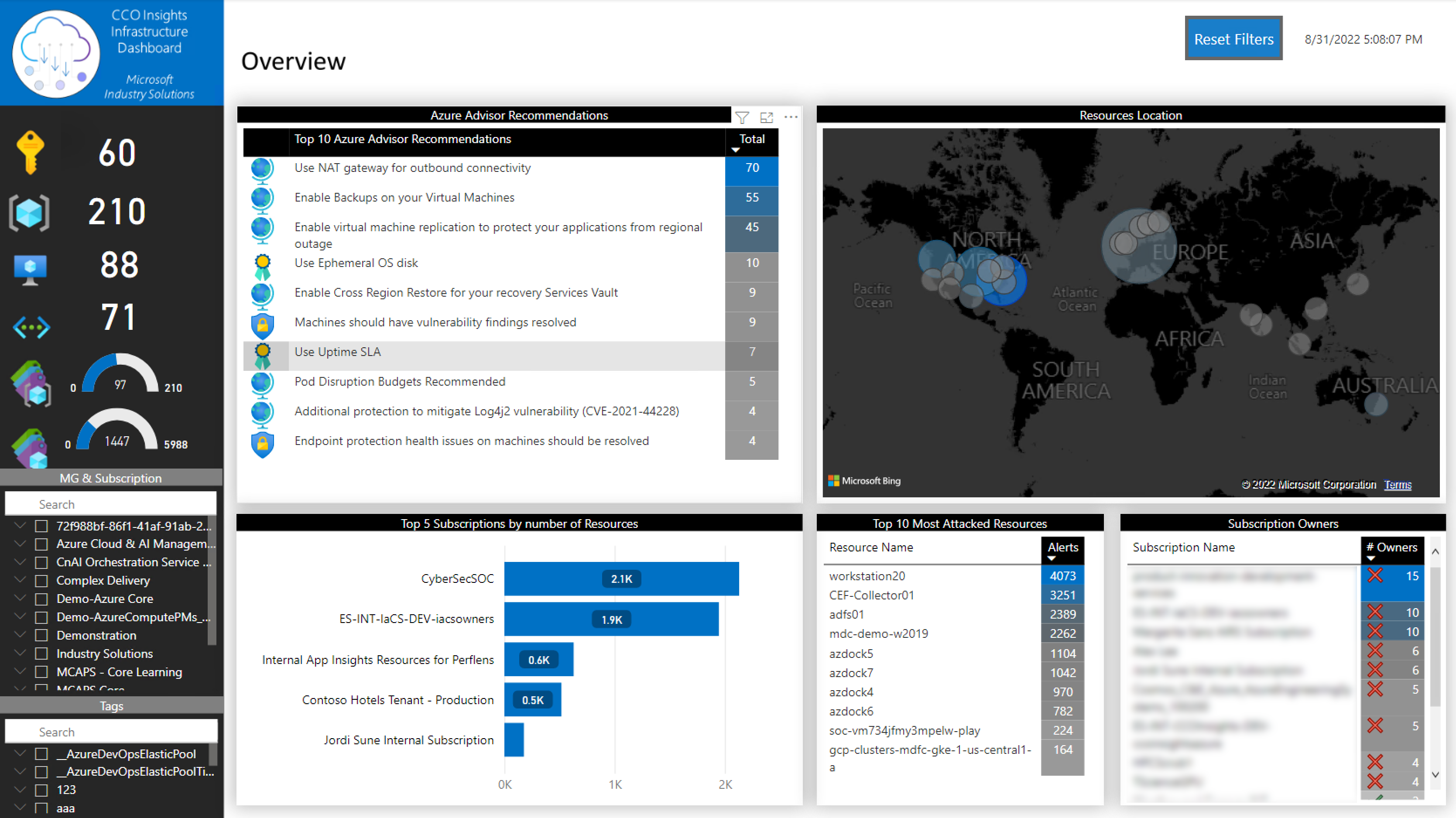
In this page, you will be able to identify the top 10 recommendations that Azure Advisor has identified, the top 10 most attacked resources and the number of subscription owners. You can also locate all the deployed resources in a map. It’s important to mention that this tab just gives you a quick view. All the recommendations will be available with more details in the following tabs.
You can filter the information by:
- Tenant
- Subscription
- Resource Tags
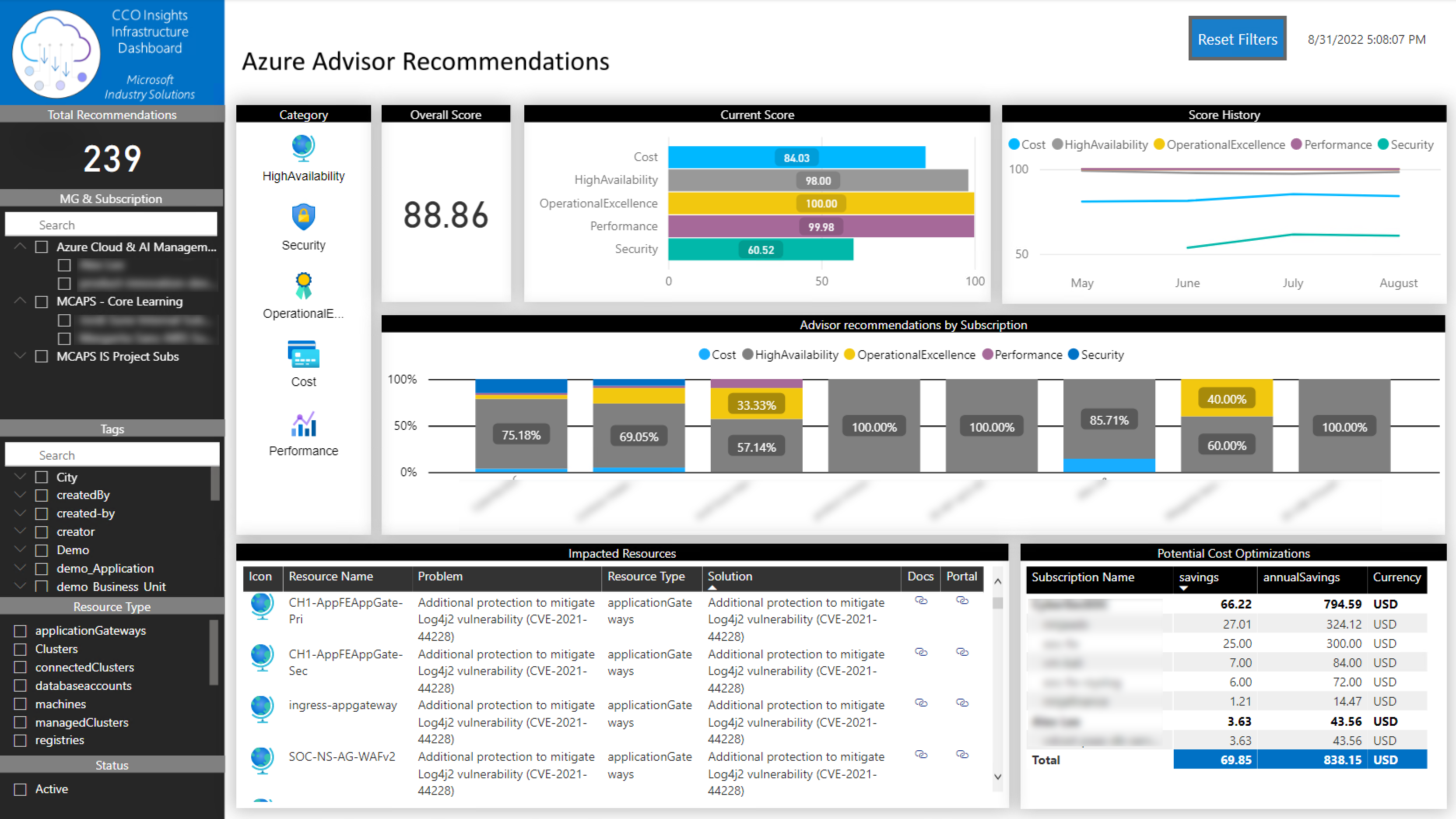
In this page of the report, you will be able to view the total amount of recommendations that Azure Advisor has identified and to what resources and subscriptions each recommendation applies to.
You can filter the information by:
- Tenant
- Subscription
- Resource type
It will also give a high-level overview of what subscriptions require more attention and has more recommendations to snooze or implement.
If you navigate to an impacted resource you will see a quick description, potential solution and in some cases a link to a website where you can find all the steps to solve the problem.
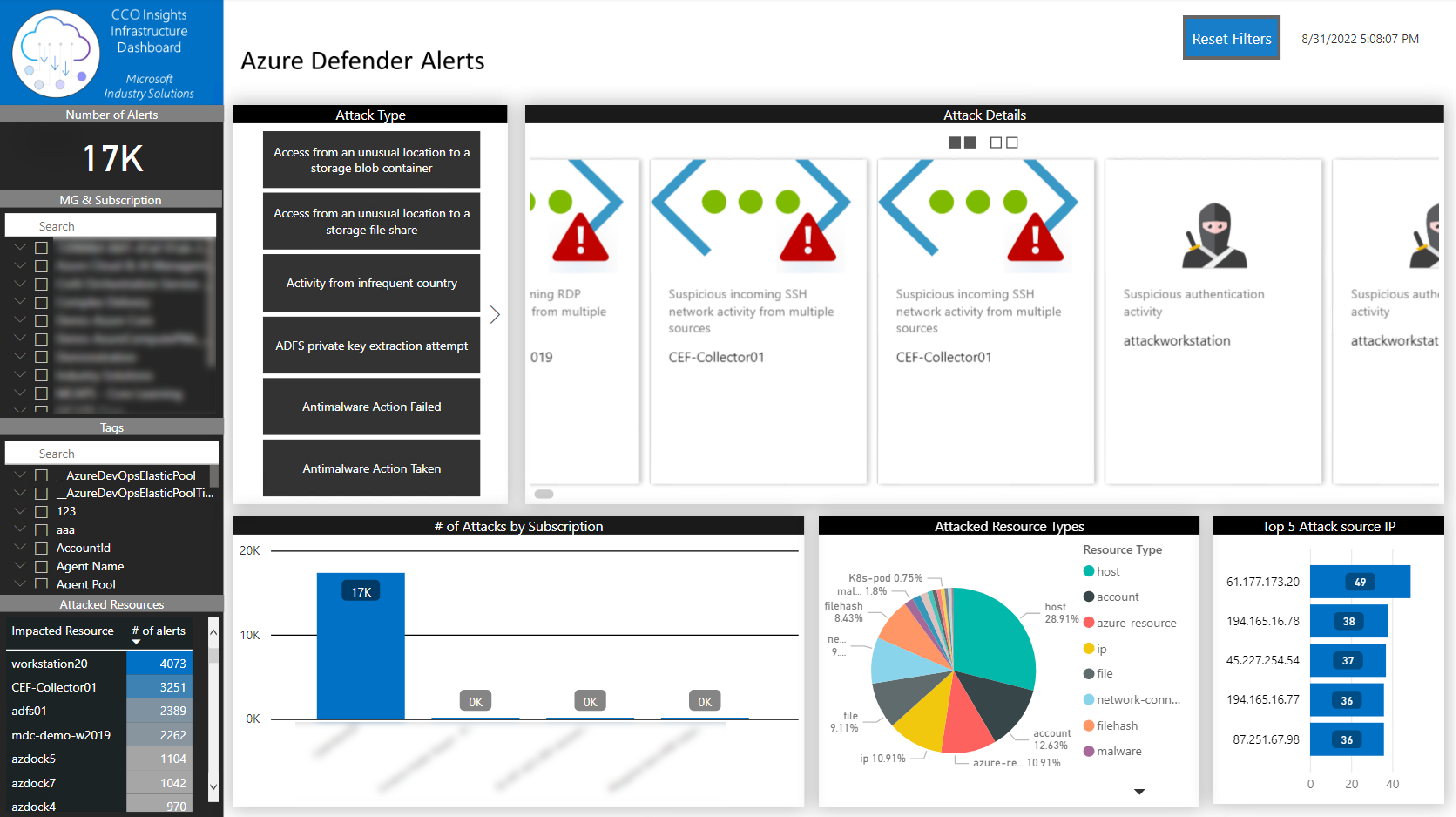
The third tab is used to show the Azure Defender Advanced Threat Analytics Alerts from all the subscriptions a given Azure account has access to. It is important to note that subscriptions will need to use the Standard plan if you want to detect and see the alerts in the Power BI Dashboard.
You can filter the information by:
- Tenant
- Subscription
- Attack type
- Data range
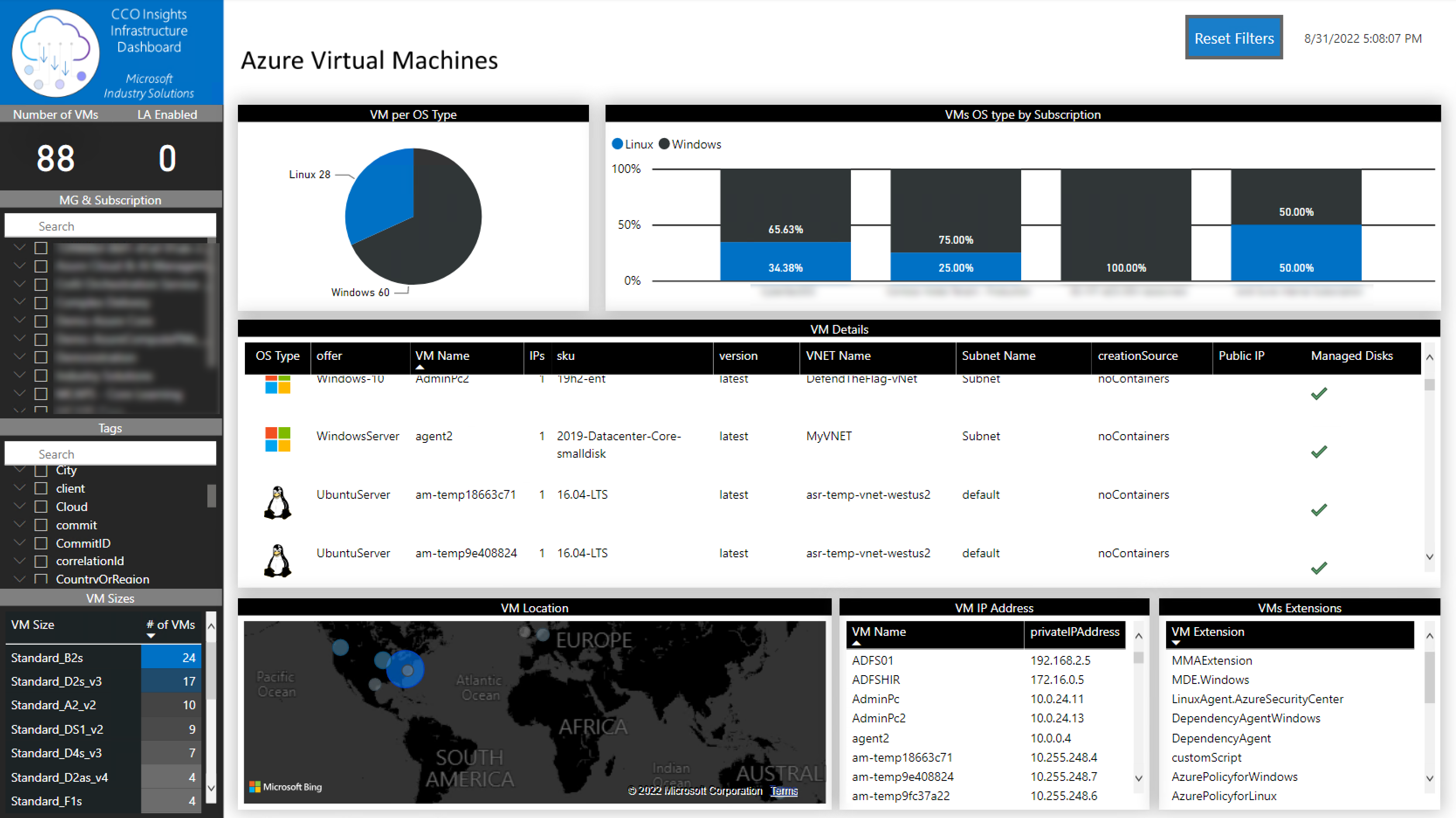
In this tab, you will be able to identify the
- number of VMs,
- the Operating System,
- the SKU,
- the Availability Set name,
- the location,
- the VM Size,
- the VNET
- and subnet each VM is connected,
- the private IP address
- and if the VM has any extension installed.
You can filter the information by:
- Tenant
- Subscription
- Resource Group
- VM extension
In this tab, you will be able to identify VNETs with only one subnet, if there are any VNET peering and if some of the subnets is exhausting its IP Pool.
You can filter the information by:
- Tenant
- Subscription
- Resource Group
- VNET
- Subnet
- Networking Interface
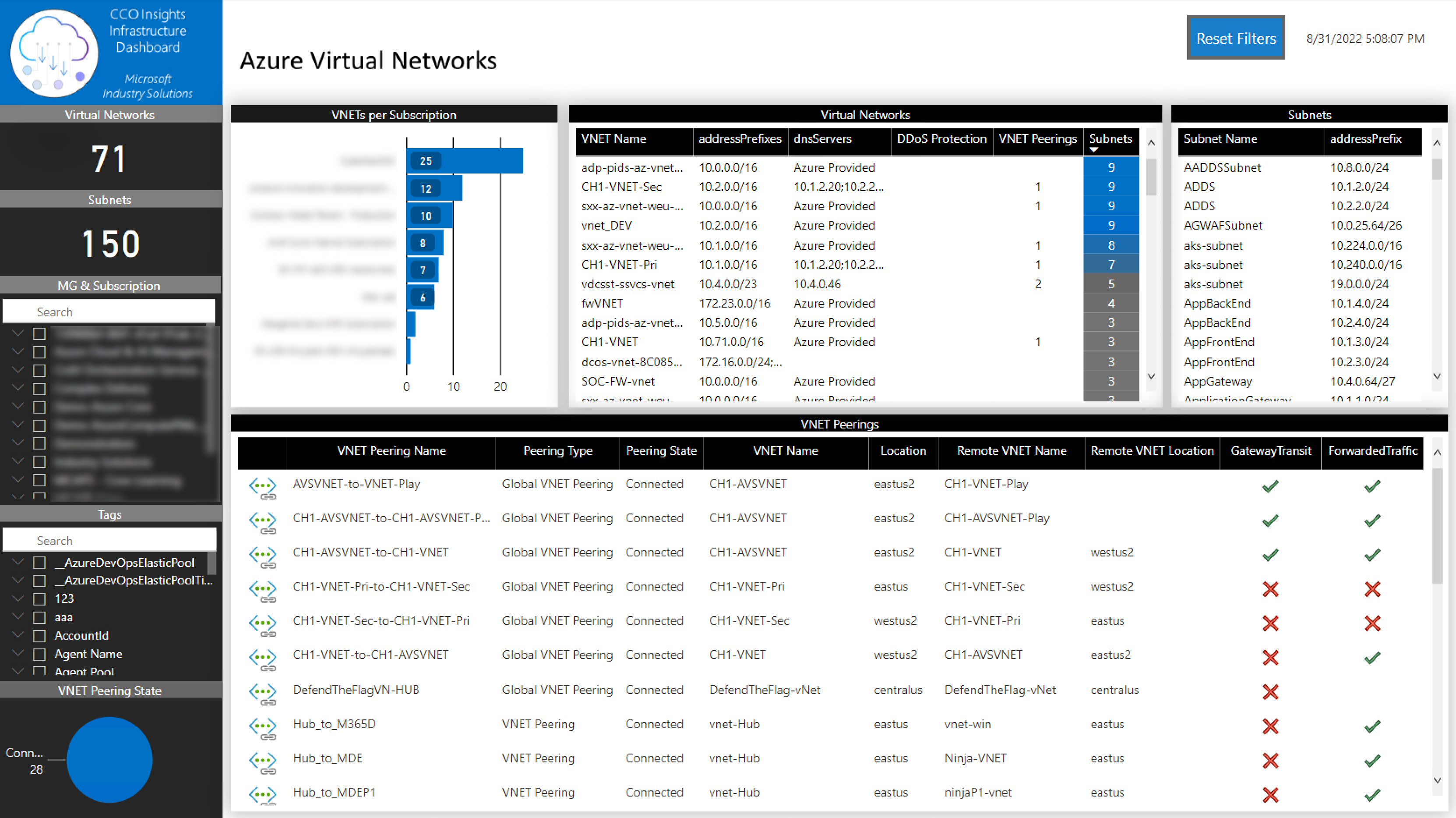
IMPORTANT: It is important to mention that although a VNET with only one subnet might not be an issue, it might be a good lead to investigate if that is the best network segmentation for the applications running on it.
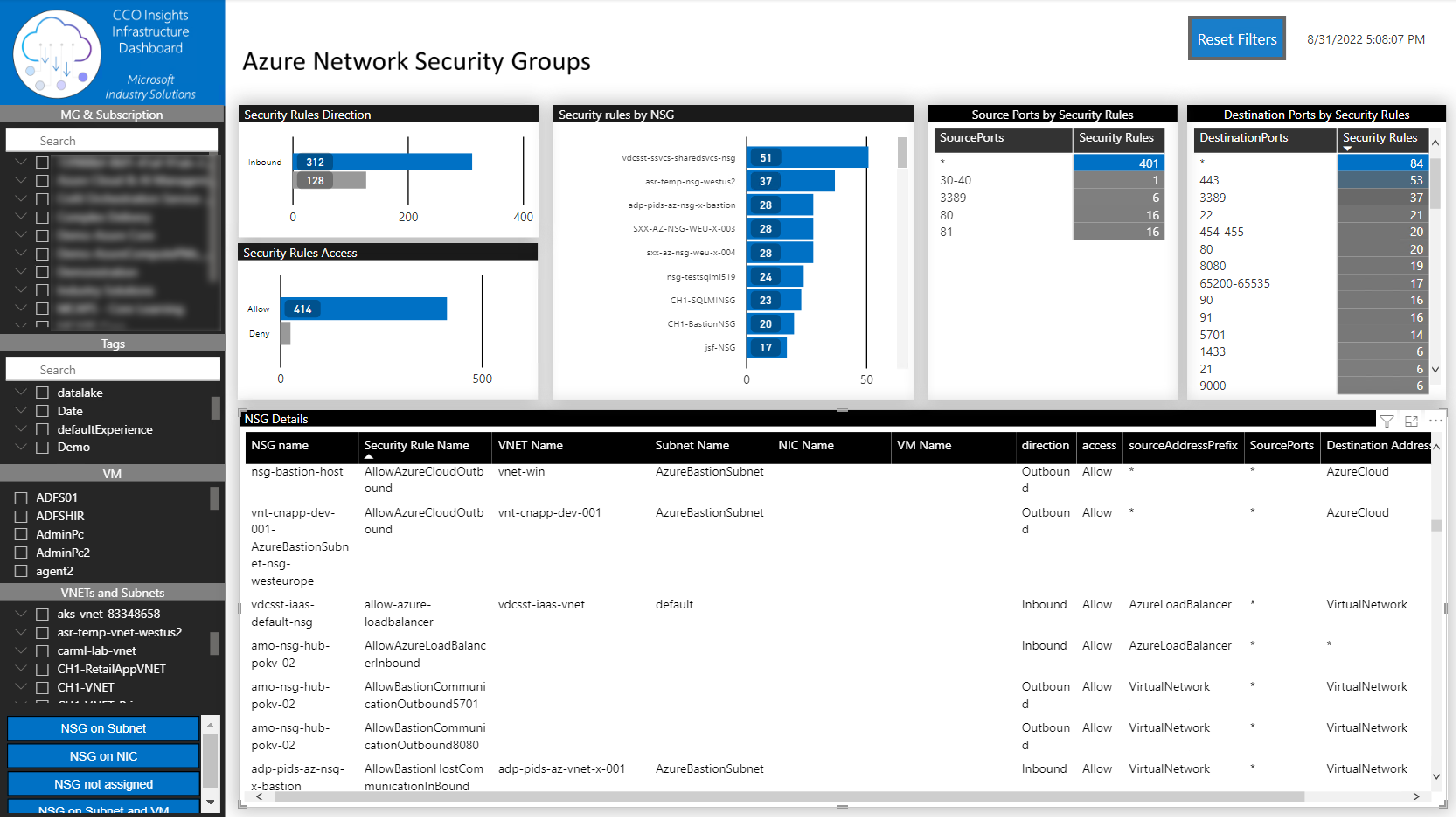
In this tab, you will be able to identify all the NSGs assigned to a VM or Subnet. On each one, you can check all the rules that are being applied.
You can filter the information by:
- Tenant
- Subscription
- VM
- VNET
- Subnet
- NSG assignment
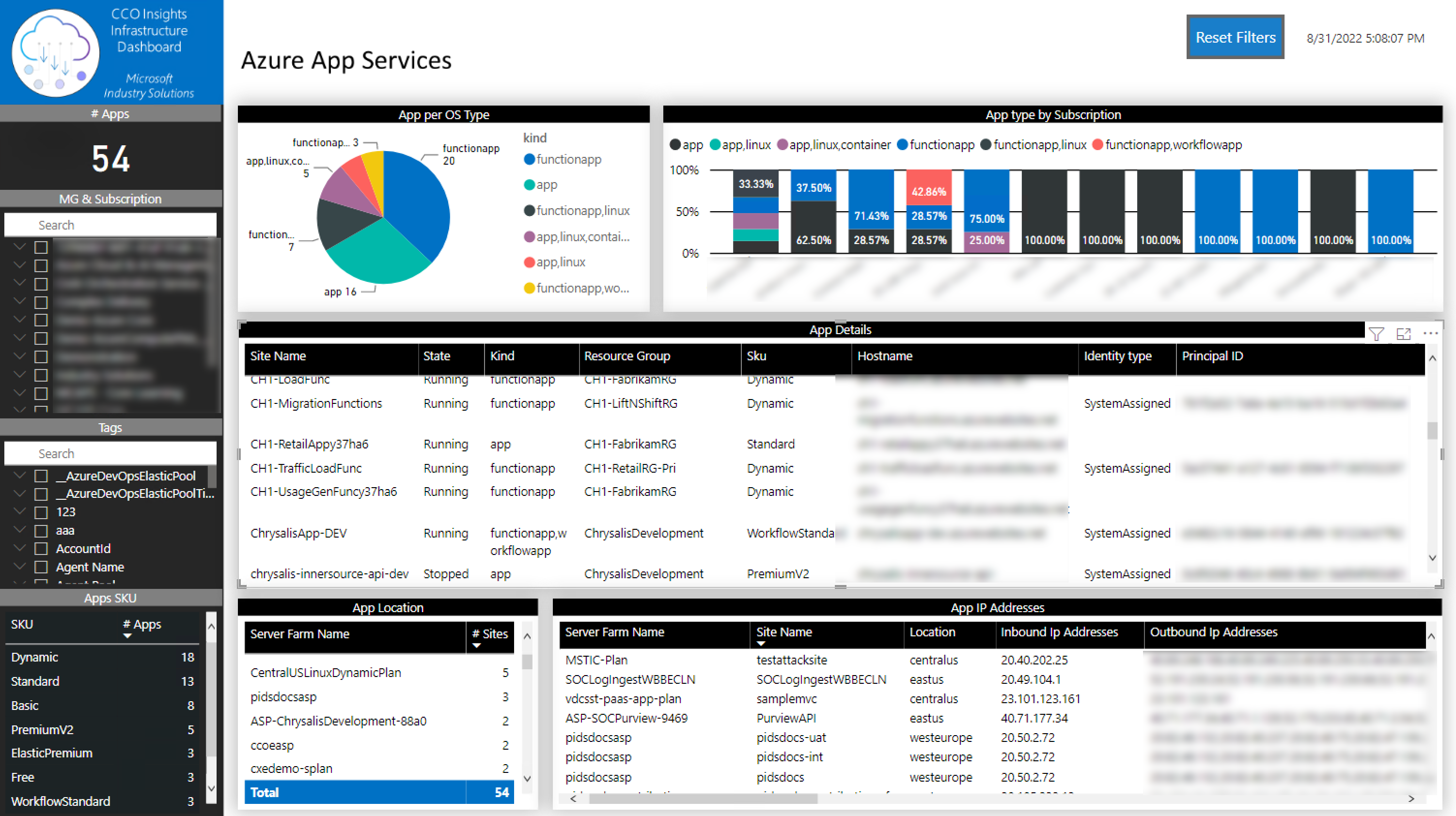
In this tab, you will be able to identify all the Application Services. On each one, you can check all the identities types, SKU and inbound and outbound IPs
You can filter the information by:
- Tenant
- Subscription
- Tags
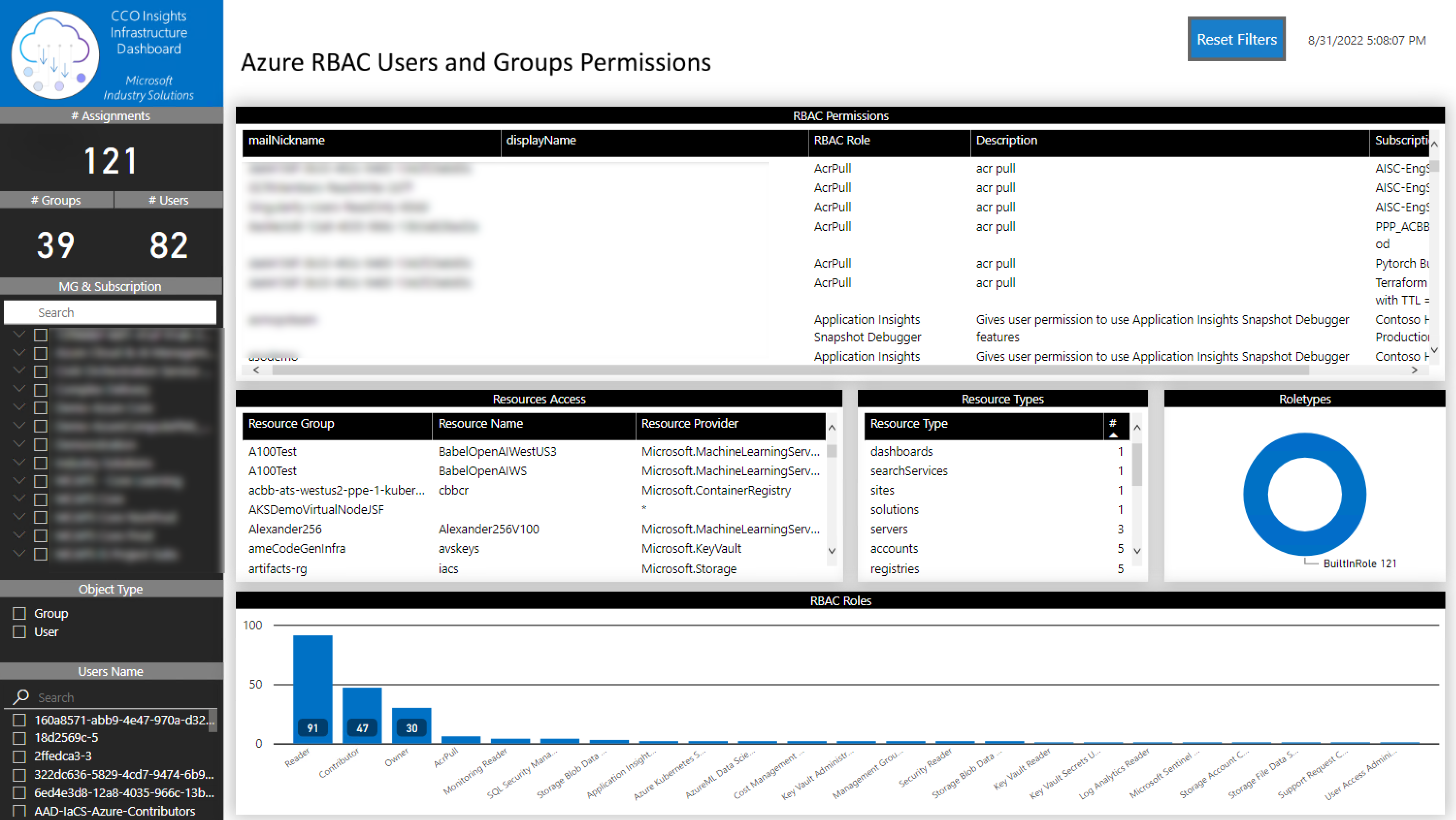
This tab is used to show the Azure RBAC permissions from all the subscriptions a given Azure account has access to. You will be able to identify the roles applied to all Azure resources and if the subscriptions have custom roles.
You can filter the information by:
- Tenant
- Subscription
- Object type
- User
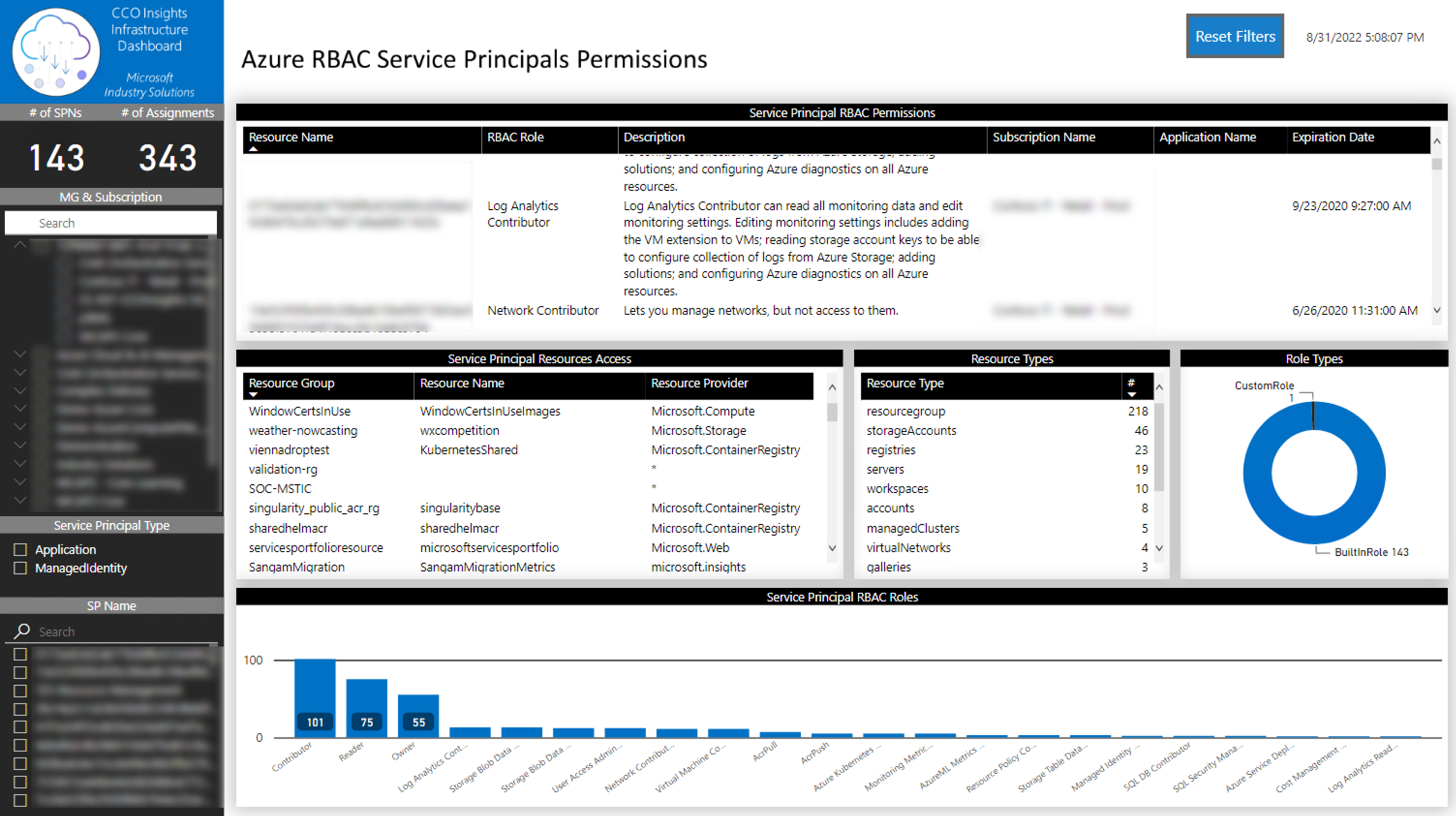
This tab is used to show Azure Service Principals RBAC permissions from all the subscriptions a given Azure account has access to. You will be able to identify the roles applied to all Azure resources and if the subscriptions have custom roles.
You can filter the information by:
- Tenant
- Subscription
- Object type
- User
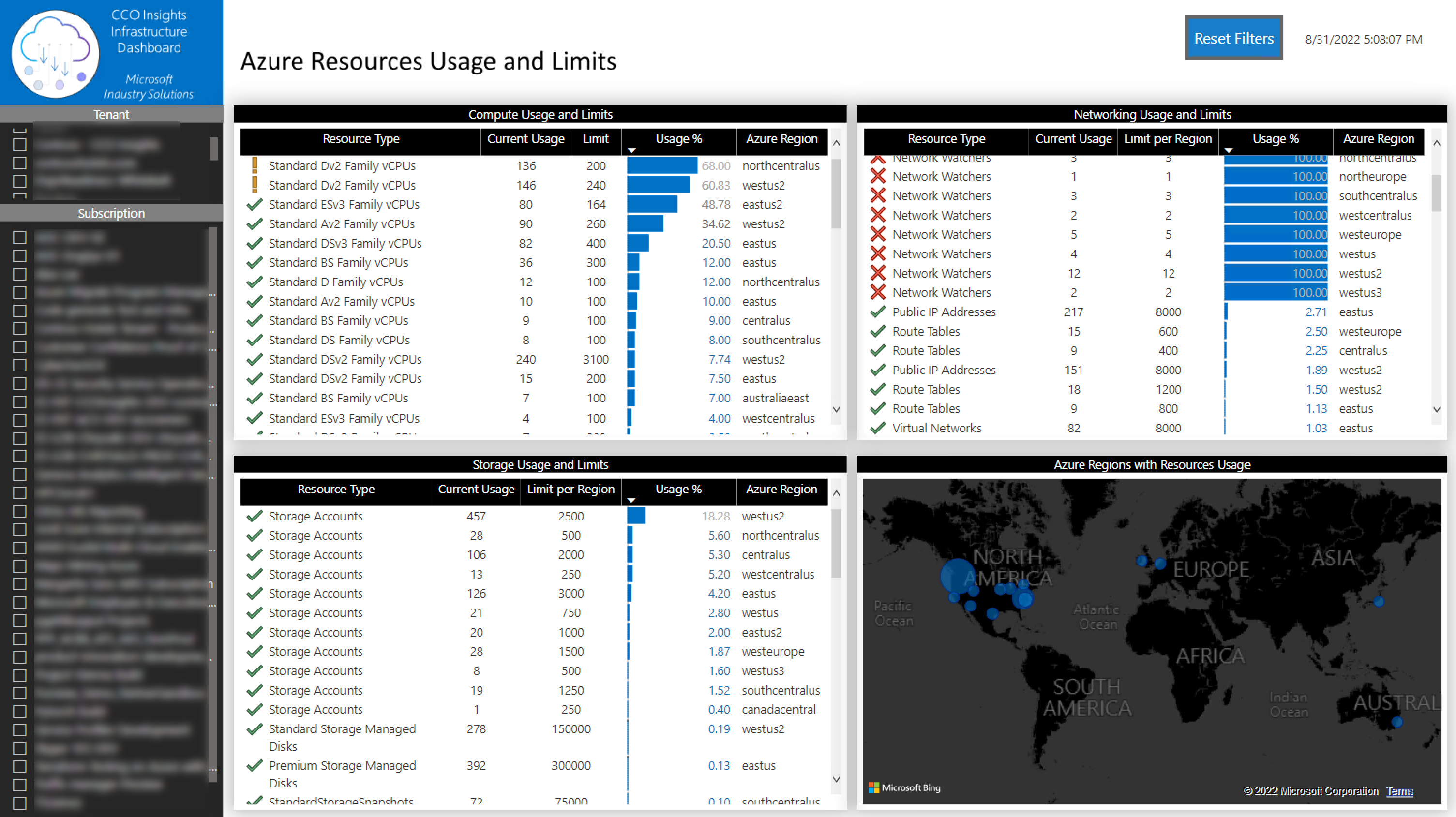
This tab allows you to identify the usage of any Compute, Storage and Networking Azure resource and validate the limits for each region and subscription.
You can filter the information by:
- Tenant
- Subscription
- Azure Region
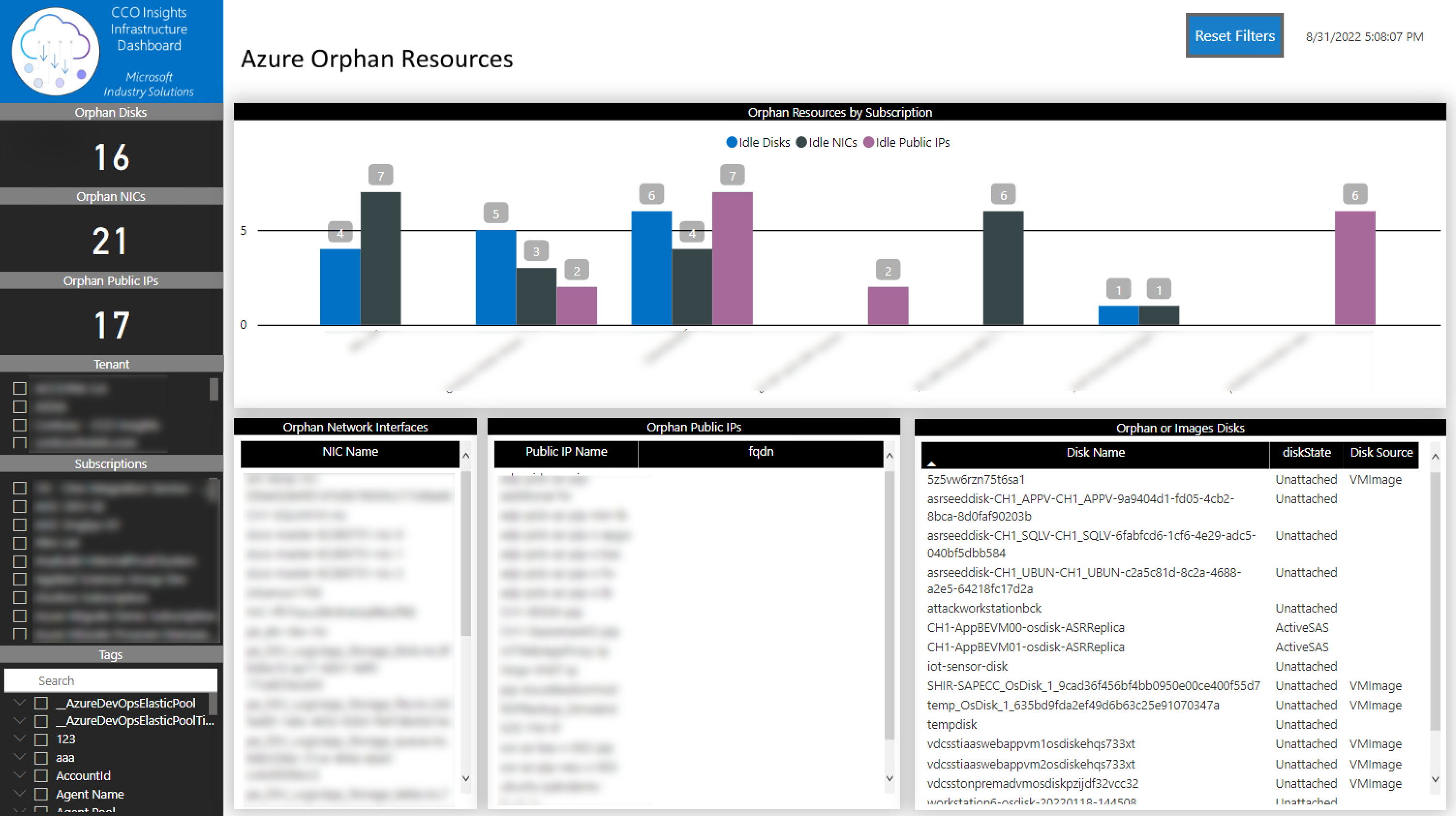
This tab lists all the Public IPs, Network Interfaces and Disks that are disconnected, idle or unattached.
You can filter the information by:
- Tenant
- Subscription
Expand this section if you want to see the Azure Kubernetes Service Dashboard information (this dashboard is currently not maintained).
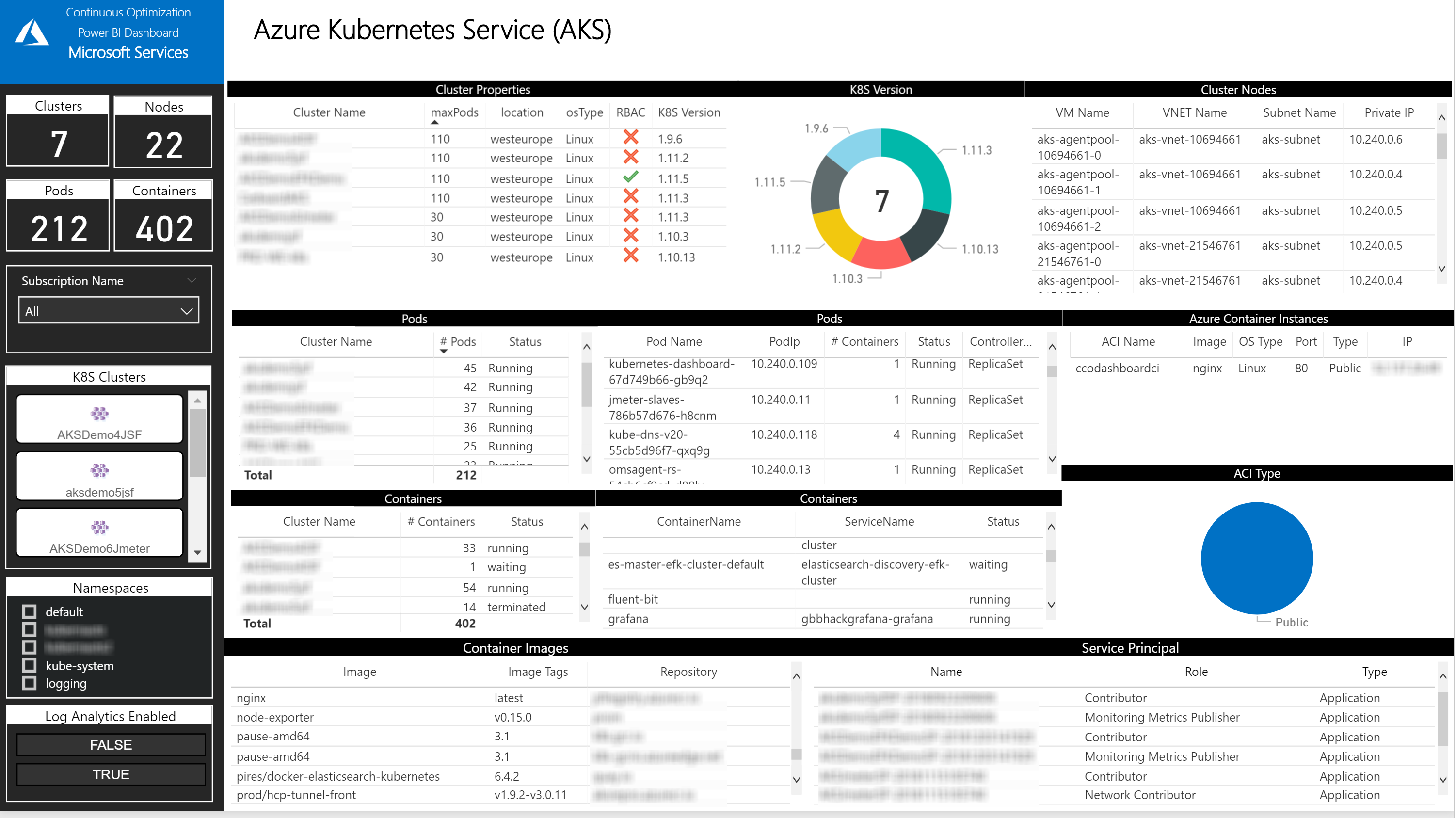
In this page, you will be able to identify the number of AKS Clusters, Nodes, Pods, Containers, Service Principals and Azure Security Center recommendations. It’s important to mention that this tab just gives you a quick view. All the detailed information will be available in the following tab.
You can filter the information by:
- Subscription
- AKS Cluster
IMPORTANT: to receive all the information related to the Pods, Containers and Container Images a log analytics workspace configured is required.
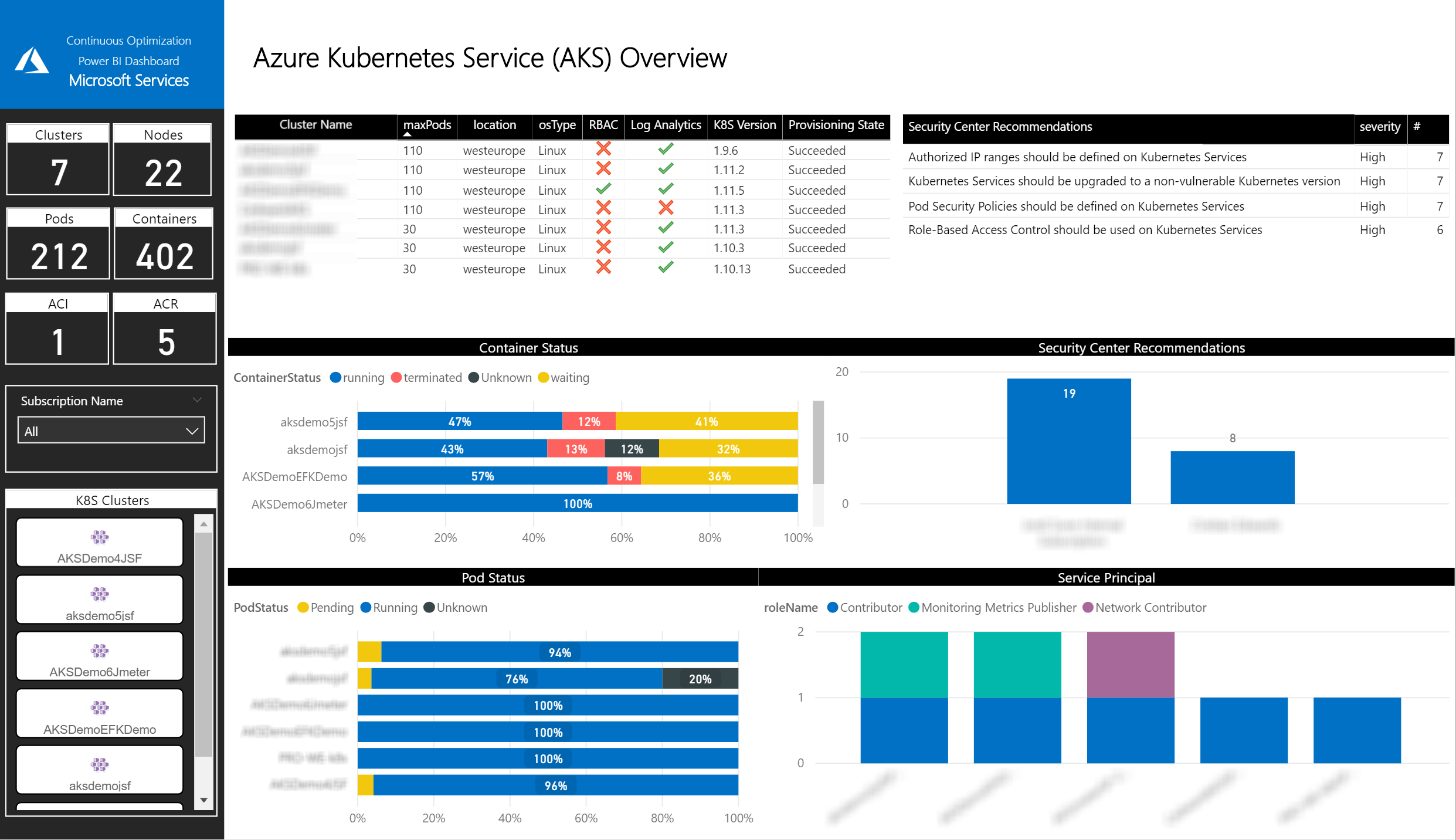
In this page, you will be able to identify the
- number of AKS Clusters,
- Nodes,
- Pods,
- Containers,
- Container images,
- Service principals
- and Azure Container Instances .
All the information related to these resources will be shown (IPs, pods in use, status, network, image repositories, RBAC roles …).
You can filter the information by:
- Subscription
- AKS Cluster
- Namespace
- Cluster Node
IMPORTANT: to receive all the information related to the Pods, Containers and Container Images a log analytics workspace configured is required.